Verizon Data Breach Investigations Report: What Are the Third-Party Risk Implications?

Verizon Data Breach Investigations Report: What Are the Third-Party Risk Implications?
By Shawn Stefanik, Intelligence Analyst
The 2019 Verizon Data Breach Investigations Report (DBIR) was released on May8th, and with it comes the annual treasure trove of lessons, use cases, and best practices to better secure your organization against threat actors of all types. As a third-party risk management leader, we looked at this year’s report through the lens of how the top third-party vulnerabilities are perpetuating breaches, and what measures can be put into place to prevent such breaches from happening. Knowing the threat landscape is important, but more important is awareness of your and your vendors’ attack surface.
Here’s what we gleaned from the report…
Web applications continue to be a top breach vector for hackers – with an increasing focus on eCommerce applications
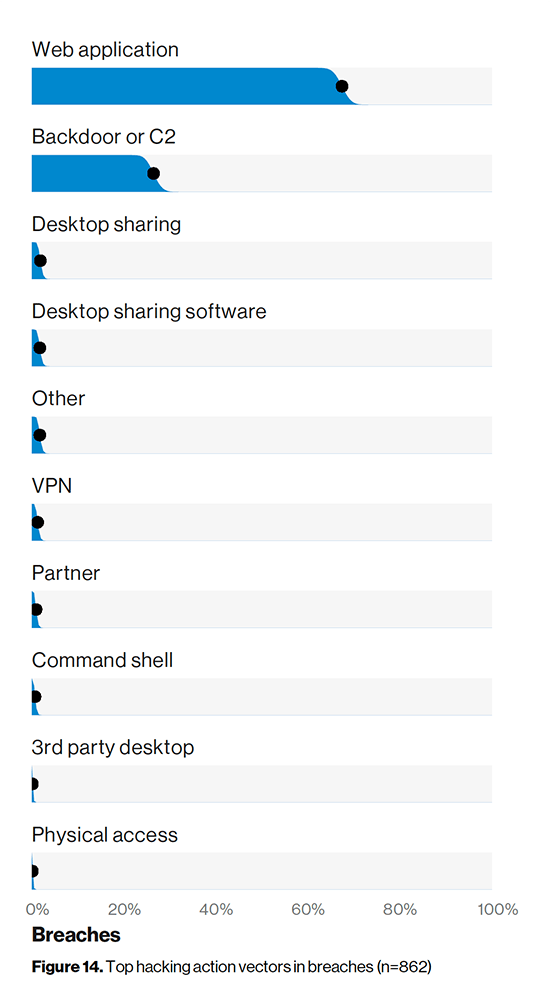
Start with figure 14 in the report, and you’ll notice that web apps continue to be the top attack vector for hackers. Attackers go after low hanging fruit. In most cases, this will be the web application, as it’s the least mature technology and therefore has the largest attack surface. Also, third-party code is used frequently across all applications even further expanding the attack surface.
Our recommendation is to use a cyber monitoring solution to review the Internet-facing web application attack surface (e.g. through external vulnerability scanning, DNS configurations, etc.) and monitor the dark web for stolen credentials attached to those apps. Both are good security practices to reduce this very real attack surface.
Prevalent’s Cyber & Business Monitoring Service includes built-in application security capabilities that perform sub-resource integrity checking—a security feature that enables browsers to verify that any resource they fetch (from a CDN, for example) and deliver has not been modified. That way, if a third-party script is compromised and malicious code is inserted, the browser will fail to load the script, since the cryptographic hash of the malicious script won’t match the known trusted hash in the integrity tag.
Use of stolen credentials is by far the number one hacking action variety
Remember above where we mentioned web applications as the top vector? Those exposed assets – combined with the number one hacking action – stolen credentials (figure 13 in the report) – pose a significant risk to organizations across all sectors. To combat this attack vector, Prevalent delivers reporting on phishing events in addition to dark web monitoring, providing some awareness of how often your vendors are being targeted and what malicious domains are being stood up as part of these campaigns. For example, we have seen situations where attackers have stood up a domain that masquerades as a login portal that customers of the vendor all share. Having this type of intelligence helps InfoSec teams blacklist the activity. See below for a screenshot of the phishing events report.

Speaking of credentials, it’s widely known that password reuse is a significant security lapse in nearly every organization. The problem is compounded when sysadmins reuse admin passwords across systems, or worse: use the same password for non-privileged and privileged accounts. Checking your vendor’s password management policies should be part of your vendor due diligence process – collected as part of a deep-controls-based assessment – helping to bring visibility to potentially bad password management practices which could be exploited to gain credentials for a breach.
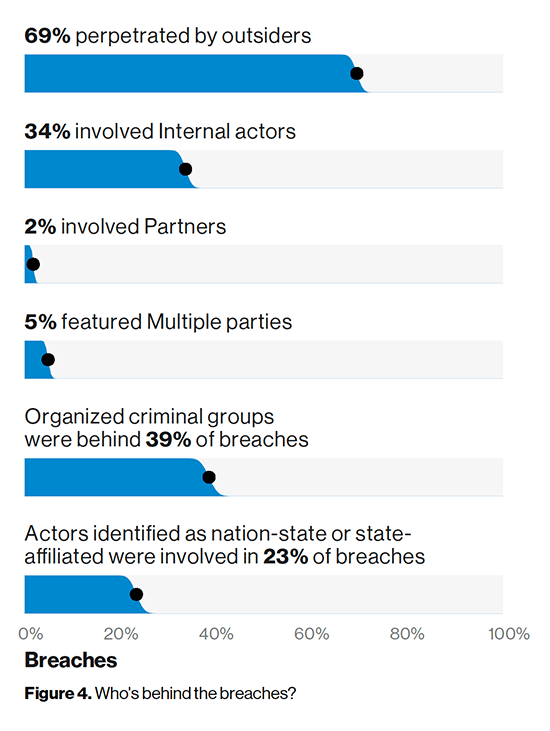
34% of breaches were perpetuated by insiders
The threat actor in breaches is internal 34% of the time—whether knowingly or unknowingly. Regularly monitoring your vendors business risks – operational, legal/regulatory, brand, and financial risks – can help reveal potential issues that could impact your business down the line. For example, layoffs increase the risk of an insider threat via a disgruntled former employee, or poor financial performance may reduce spending on cybersecurity and subsequently user security awareness and training may be hampered.
Prevalent utilizes an industry-unique combination of technology, data analytics, and human analysts to deliver business risk assessments. Prevalent analysts collect, categorize, and score based on rules derived from a combination of methods including commercial due diligence, financial analysis, and cyber threat intelligence. With backgrounds in national security and cyber threat intelligence, Prevalent cyber analysts provide geopolitical context and fluency in seven languages.
Next steps
Insights from continuous monitoring can and should be used both internally and alongside results of internal controls-based assessments for a complete picture of your critical vendors that may have access to sensitive systems and data. In this blog we reviewed four such use cases: scanning for web application vulnerabilities and for stolen credentials on the dark web, assessing password policies, and monitoring for potential risks stemming from business events. For more on how Prevalent can help you centralize your view of third-party risk management – delivering a unified outside-in and inside-out approach to improving security and meeting compliance requirements, contact us today for a demo.
-

Third-Party Data Breaches: What You Need to Know
Why third-party breaches are on the rise, who is being affected, and what you can do...
01/07/2025
-

SIG 2025: Key Updates and Considerations
Uncover key changes in the Standard Information Gathering (SIG) Questionnaire for 2025 and learn what these...
12/16/2024
-

Preparing a Third-Party Incident Response Plan
Effectively manage third-party cybersecurity incidents with a well-defined incident response plan.
09/24/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo



