Vendor Risk Assessment: The Definitive Guide

Vendor risk assessments are a critical component of third-party risk management programs. When leveraging third-party solutions and services, it's important to understand the potential risks they can introduce to your organization. These include cybersecurity, data privacy, compliance, operational, financial, and reputational risks. Conducting assessments can help you to reveal and remediate these risks throughout the vendor lifecycle.
Vendor risk assessments enable your organization to proactively identify and mitigate third-party risks and help it be better prepared for when incidents do occur. Well-managed assessments can strengthen vendor relationships, demonstrate proper due diligence to regulators, and shed light on best-practice security controls.

What Is a Vendor Risk Assessment?
A vendor risk assessment is a process companies use to evaluate potential risks when working with third parties such as vendors, suppliers, contractors, or other business partners. It involves assessing risks during different stages of the vendor relationship, from sourcing and selection to offboarding and termination.
Assessments typically include gathering information about the vendor's security, privacy controls, financial and operational data, and policies, often through questionnaires. The identified risks are then rated based on severity, likelihood, and other factors. Results are often mapped to regulatory requirements, compliance standards, and security frameworks, such as ISO and NIST.
Vendor risk assessments look at a variety of factors during the different stages of the vendor management lifecycle, including:
- During sourcing and selection, to identify and shortlist low-risk vendors
- During onboarding, as due diligence to gauge inherent risk before granting access to critical systems and data
- On a periodic basis, to check SLAs, evaluate contract adherence, or satisfy audit requirements
- During offboarding, ensure that system access is terminated and that data has been protected or destroyed according to regulations
- During incident response to determine the potential scope and impact of security breaches
Vendor Risk Assessment Explained
Watch this video to learn how vendor risk assessments enable you to proactively identify and mitigate third-party risks and be better prepared for when incidents occur.
Why Are Vendor Risk Assessments Essential?
In recent years, the world has experienced major business and supply chain disruptions from the ongoing COVID-19 pandemic, extreme weather events, increasingly significant cyber attacks, and other events. As a result, organizations faced operational breakdowns, financial losses, and legal actions. While many of these events were not preventable, organizations with effective third-party risk management (TPRM) programs were often able to significantly reduce or mitigate their impacts.
Implementing third-party risk assessment workflows that focus on operational risks, business continuity, and security risks can enable your organization to streamline procurement processes, improve supply chain resilience, and satisfy compliance audits. What's more, the cost to build and maintain a strategic third-party assessment practice is far less than the potential damage high-risk vendors can cause.
What Are the Different Categories of Vendor Risk?
There are three primary types of risk when dealing with third parties: profiled risk, inherent risk, and residual risk. Here is a brief breakdown of the three:
- Profiled Risk relates directly to the vendor's relationship with your organization. Certain vendors pose more risks. For example, a credit card processing company likely poses substantially more risk to your organization than a digital advertising agency. Organizations with a higher level of profiled risk require extra scrutiny during vendor selection.
- Inherent Risks refer to risks that the vendor poses due to its own information security, operational, financial, and other business practices prior to implementing any controls required by your organization. Determining a potential vendor’s inherent risk score requires a combination of detailed vendor assessment questionnaires and external threat monitoring.
- Residual Risk is the level of leftover risk once the organization in question has implemented your organization’s mandatory controls. Residual risk can never be eliminated, but it can be brought to a level that the organization deems acceptable.
How Do You Score Vendor Risks?
The basic calculation for scoring vendor risk is Likelihood x Impact = Risk. For example, let's say a hospital vendor is processing large amounts of protected health information (PHI) but not complying with HIPAA. Under HIPAA, they would be classified as a business associate and fall under the same regulatory scrutiny as the healthcare provider. In this case, the impact is a large fine to both the healthcare provider and the business associate (e.g., major or severe impact), and the likelihood is chance that their non-compliance would be discovered by regulators (e.g., likely or extremely likely). This would represent an unacceptable risk for any healthcare organization and would likely result in the termination of the contract.
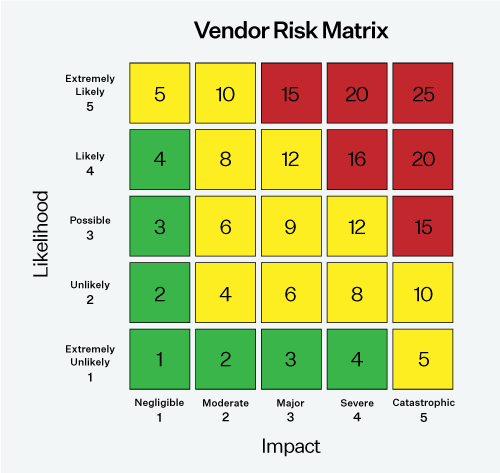
The above example highlights the importance of conducting thorough vendor risk assessments. This is even more important for organizations dealing with large amounts of sensitive data, such as government contractors and healthcare providers. In many cases, regulations such as HIPAA will hold the primary organization responsible for vendor non-compliance.
Vendor Risk Assessment Steps
1. Assemble Internal Stakeholders
The most successful vendor risk assessment programs involve stakeholders' input and/or participation, representing multiple roles with different priorities. These can include:
| Role | Example Priorities |
|---|---|
|
Unifying vendor assessments with broader organizational risk management initiatives and integrating third-party risk data with GRC platforms. |
|
|
Sourcing low-risk vendors, conducting pre-contract due diligence, assessing supplier performance, and ensuring that contractual obligations are met. |
|
|
Identifying, analyzing, and remediating cybersecurity risks connected to third parties. |
|
|
Understanding and reporting on vendor risk in the context of government regulations and industry frameworks. |
|
|
Identifying which vendors handle private data, conducting privacy impact assessments, and reporting against privacy compliance requirements. |
Assembling a cross-functional team to plan and guide your assessment program will help to ensure its organizational adoption and long-term success.
2. Define Your Acceptable Level of Residual Risk
In a perfect world, risk could be eliminated entirely. Unfortunately, when working with any third party, there will always be some element of risk. Before assessing potential vendors for a project, you need to define what level of risk is acceptable. This can make vendor selection and the entire third-party risk management process faster, more efficient, and more uniform. This enables you to easily identify vendors that clearly won’t meet your business objectives and risk tolerance. In addition, it can help clarify which controls you need to require of vendors before working with them.
3. Build Your Vendor Risk Assessment Process
Implement a process with standardized controls and requirements. However, there is no one-size-fits-all approach to vendor risk assessment. Different vendors present varying levels of risk to your organization, depending on factors such as:
- Their importance to your supply chain, especially if they are a single-source or sole-source supplier.
- Their access to sensitive data, such as personally identifiable information (PII), protected health information (PHI), or commercially sensitive information (CSI).
- Their vulnerability to disruptions, like natural disasters or geopolitical conflicts.
Begin with an internal profiling and tiering assessment to categorize your vendors and determine the type, scope, and frequency of assessment needed for each group. For instance, vendors critical to your business and with high-risk potential (e.g., accounting firms or sole-source suppliers) require more thorough due diligence than those with lower-risk profiles (e.g., advertising firms).
Having a structured process for each vendor category makes your third-party risk management program more efficient and helps you make better risk-based decisions about your vendor relationships.
4. Send Vendor Risk Assessment Questionnaires
The next step is to select and send risk assessment questionnaires for each vendor or category of vendor. Questionnaires provide a trust-based approach to gathering information about each vendor's internal controls. They can cover a variety of topics, including information security practices, compliance requirements, financial stability, and fourth—and Nth-party supplier data.
Selecting a Questionnaire
One of the biggest choices companies face when selecting questionnaires for their primary risk assessments is whether to use an industry-standard questionnaire, such as the Standard Information Gathering (SIG) questionnaire, or a proprietary questionnaire. In some cases, your third parties may already have an information security certification, such as CMMC or SOC 2. You may accept these certifications instead of requiring an assessment response or supplement them with proprietary and/or ad-hoc assessments to gather information about specific controls or potential risks outside of cybersecurity. For more about the pros and cons of each assessment approach, read our post on selecting a vendor risk assessment questionnaire.
Choosing a Framework
Many organizations choose to employ frameworks when designing their vendor assessment questionnaires, such as the NIST Cybersecurity Framework, ISO 27001, and NIST 800-30, to ensure that questionnaires are standard across the supply chain and reflect best practices. If you require your suppliers to be compliant with specific regulations such as the GDPR or PCI DSS, it may be worth incorporating questions around those standards directly into your vendor risk management program.
Free Template: Top 20 TPRM Questions (XLS)
Use this free third-party risk questionnaire to jump start your third-party risk assessment process with the top 20 control questions to ask vendors.

5. Complement Assessments with Continuous Risk Monitoring
Cybersecurity vulnerabilities, supply chain challenges, and compliance requirements evolve continuously. Therefore, be sure to conduct continuous risk monitoring to catch any cyber, business, or reputational risks that arise between your periodic vendor assessments. You can also use risk data to verify that a third party's assessment responses are consistent with their real-world business activities.
Vendor Data Breaches, Exposed Credentials, and other Cyber Risks
Third-party data breaches, ransomware attacks, and other cyber incidents are constant and pervasive threats to organizations today. Therefore, conducting external monitoring of cybersecurity risks across your vendor ecosystem is critical. Key risks to look out for include:
- credential exposures
- data breaches and confirmed incidents
- web application misconfiguration and vulnerabilities
- typosquatting and other brand threats
Supplier Finances, Business Practices and Reputation
While third-party breaches and cybersecurity incidents tend to monopolize the headlines, a supplier's financial failure, operational disruptions, or bad press can have serious implications for your business. These "non-IT" risks also extend to environmental, social, and governance (ESG) challenges, like modern slavery, bribery/corruption, and consumer protection issues.
Look for news reports, financial information, and fourth-party relationships that could signal problems. Examine suppliers' business practices, raw material sourcing, and other key business processes that could pose reputational or ethical concerns to your business. In addition, ask for reference customers and partners that utilize the third party's products and services. Speak with references to gain further insights into the third party's ability to deliver against SLAs and other contractual obligations.
Selecting a Monitoring Strategy
From open-source intelligence to public websites, there is no shortage of places to find intelligence on your third parties. However, building a comprehensive and efficient monitoring program from scratch can be difficult. Many companies leverage automated vendor threat monitoring software for risk identification and scoring.
6. Categorize and Remediate Risks
Risks can be categorized as either acceptable or unacceptable. Unacceptable risks must be remediated prior to working with the vendor. Remediating Third-Party Risks can take various forms. An organization may choose to ask a potential vendor to achieve a security certification such as SOC 2, cease relationships with 4th and Nth-party vendors, or change business practices that could cause supply chain or other disruptions.
In addition, organizations should have a third-party incident response strategy in the event that a vendor suffers a data breach or other disruption. Having a defined strategy for dealing with risks that materialize can dramatically cut down on the time it takes to mount an effective response and reduce disruption to your organization.
Vendor Risk Assessment: The Definitive Guide
Download this 18-page guide to gain comprehensive guidance on how to conduct and implement vendor risk assessments at your organization.

How to Start a Vendor Risk Assessment Program
One mistake many companies make when launching an assessment program is relying on email and spreadsheets to get the job done. Unless you only work with a handful of vendors, this manual approach to assessments can be a nightmare for auditors and vendors – while delivering little useful data.
If you’re looking to launch an assessment program, a great place to start is by subscribing to a vendor intelligence network, which offers access to a library of vendor risk reports based on standardized assessment data. Then, for increased customization and control, consider an automated vendor risk assessment solution that enables you to conduct and manage your assessment initiatives. Or, if you prefer a more hands-off approach, a managed service provider can conduct assessments on your behalf.
Next Steps
Prevalent offers vendor risk assessment solutions and services as part of our comprehensive third-party risk management platform. To discuss your specific needs with a Prevalent expert, request a personalized demo today.
-

Third-Party Risk Management: The Definitive Guide
Third-Party Risk Management (TPRM) has advanced from being an annual checklist exercise to a critical daily...
01/23/2025
-

Vendor Due Diligence Strategy and Checklist
With a mature vendor due diligence strategy, businesses can assess risks early, categorize vendors accordingly, and...
01/16/2025
-

The Top 7 TPRM Predictions for 2025
2025 promises to be a consequential year for third-party risk management. Read our top TPRM predictions...
12/12/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




