Understanding Inherent Risk vs. Residual Risk

In the intricate landscape of Third-Party Risk Management (TPRM), distinguishing between inherent and residual risks is crucial for formulating an effective risk analysis and mitigation strategy. This blog defines inherent and residual risks, examines their significance in TPRM, and explores best practices for incorporating these risk categories into your third-party risk management program.
What Is Inherent vs. Residual Risk?
Inherent risks are innate, unaddressed liabilities that an organization may encounter when working with vendors, suppliers, or other third parties. Residual risks are those exposures that remain after the application of initial controls.
Inherent Risk
Think of inherent risk in terms of the standard features and potential vulnerabilities that come with a newly purchased car. For instance, while the car might be fast and reliable, it might also come with the inherent risk of being a model that is frequently targeted by thieves.
In the context of third-party risk, inherent risk refers to the exposures that a vendor or supplier poses to your organization at the start of the business relationship. These potential risks could be related to the nature of the services they provide, their financial stability, or their information security posture.
Residual Risk
Residual risk is the risk that exists after the implementation of required mitigations or internal controls. Continuing with the car analogy, you could install an advanced security system and park the car in a secure garage to minimize the chances of theft or damage. Despite these measures, residual risks still exist – such as the possibility of a natural disaster or advanced hacking attempt.
In the world of third-party risk management, residual risk is what remains after implementing acceptable risk mitigation measures and controls – for example, the purchase of a cyber insurance policy or the application of a critical software patch. Your organization’s risk tolerance may vary depending on the potential impact and likelihood of each residual risk.
The Significance of Inherent and Residual Risks in TPRM
Identifying inherent risks is akin to having a radar that detects potential threats on the horizon and enables you to take preventative measures. By comprehending the baseline risks associated with a vendor, organizations can initiate targeted assessments and conduct appropriate due diligence. This early identification enables the strategic allocation of resources, directing attention to areas of higher inherent risk. It acts as the foundation upon which risk management strategies are built, offering insights into potential vulnerabilities that need proactive attention.
Residual risks, on the other hand, play a crucial role in maintaining the ongoing health of the third-party relationship. While inherent risks provide the starting point, residual risks are the indicators of how well the implemented controls are working. They guide organizations in determining the effectiveness of their risk mitigation strategies, helping them adapt and refine their approach based on evolving threats and changes in the vendor landscape. Residual risks act as the compass, steering TPRM efforts toward sustained resilience.
Incorporating Inherent and Residual Risks into Your TPRM Program
Holistic Vendor Profiling
Begin by building a comprehensive risk profile for each vendor in your ecosystem. Understand the nature of their services, their criticality to business operations, the data they handle, financial and reputational measures, and their industry compliance factors. This profiling not only aids in assessing inherent risk but also forms the basis for tiering vendors for subsequent risk assessments.
Leverage TPRM software to automate the profiling process, making it efficient and scalable. Automated profiling questionnaires, distribution, and response workflows streamline the onboarding process, enabling you to manage and update profiles seamlessly throughout the vendor lifecycle. A comprehensive vendor profile should also layer in externally observable risk metrics such as ESG scores, financial ratings, CPI scores, and other insights to help teams understand a supplier’s full inherent risk picture.
Structured Risk Scoring
Implement a structured risk scoring system that quantifies risk factors such as financial stability, security practices, and operational efficiency. Consider a scoring matrix that combines likelihood and impact to assess the effectiveness of controls. This provides a quantitative basis for decision-making and resource allocation.
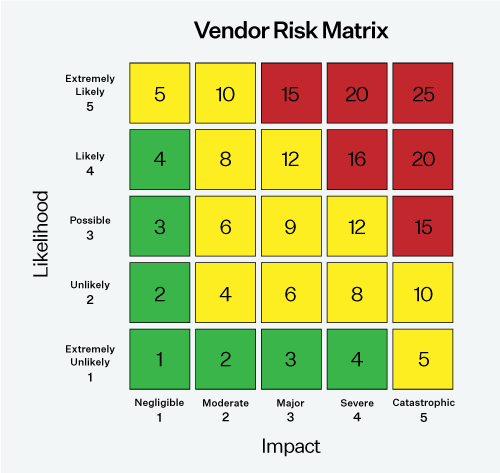
Utilize a matrix that combines likelihood and impact to determine the risk scores.
Tiering and Categorization
Start with an internal profiling and tiering assessment to help categorize your vendors and map out the type, scope and frequency of assessments required for each group. Having a structured process for each vendor category will enable your third-party risk management program to operate more efficiently and enable you to make better risk-based decisions about your vendor relationships.
Leverage tiering based on inherent risk assessments to prioritize resources and efforts. High-risk vendors, such as billing or payroll providers, may undergo more extensive assessments and monitoring. For residual risks, tailor risk mitigation strategies according to the tiered categorization, focusing resources on high-risk vendors to ensure sustained compliance and risk reduction.
Continuous Monitoring
Given the ever-evolving threat landscape, continuous monitoring is indispensable. Incorporate external threat intelligence services to verify assessment responses, identify discrepancies, and fill the gaps between point-in-time assessments. Regularly monitor the effectiveness of security controls to mitigate inherent risks and compensate for residual risks.
Leverage a TPRM platform that offers real-time monitoring and alerts via continuous external vendor risk monitoring. The ability to stay on top of external events and receive alerts about new and emerging risks enables swift responses and proactive risk management.
Collaborative Remediation Initiatives
Engage in collaborative efforts with vendors to address inherent risks through security assessments, compliance checks, and ongoing communication. For residual risks, facilitate continuous collaboration to ensure that compensating controls remain robust and aligned with evolving threats. This ongoing partnership is vital for sustaining a secure third-party ecosystem.
A third-party risk management platform can facilitate this collaboration with vendors to streamline the remediation process. A platform with robust vendor risk management workflows and reporting capabilities ensures seamless communication and collaboration between your team and vendors. Built-in recommendations streamline the remediation process and enhance the overall effectiveness of your risk management strategy.
Incident Response
Finally, organizations should have a third-party incident response strategy for when a vendor suffers a data breach or other disruption. Having a defined strategy for dealing with breaches or other incidents can dramatically cut down on the time it takes to mount an effective response and reduce disruption to your organization. Plus, a record of prior incidents helps to inform ongoing assessment strategies and influences residual risk.
Next Steps for Managing Inherent and Residual Risk
Effectively managing inherent and residual risks is a necessity for organizations aiming to thrive in an increasingly interconnected business environment. By defining these concepts, recognizing their significance, and incorporating best practices into your risk management strategy, your team can navigate the complex landscape of third-party relationships with confidence and resilience. Learn how Prevalent can help you automate and streamline this process. Request a demo today.
-

Third-Party Risk Management: The Definitive Guide
Third-Party Risk Management (TPRM) has advanced from being an annual checklist exercise to a critical daily...
01/23/2025
-

Vendor Due Diligence Strategy and Checklist
With a mature vendor due diligence strategy, businesses can assess risks early, categorize vendors accordingly, and...
01/16/2025
-

The Top 7 TPRM Predictions for 2025
2025 promises to be a consequential year for third-party risk management. Read our top TPRM predictions...
12/12/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




