How to Improve Third-Party Risk Management Program Maturity

In an increasingly connected business world, it is no longer acceptable to ignore risks to your organization from poor security practices among your partners, vendors, or suppliers. Cyber criminals understand that the simplest way to breach an organization is through its third parties.
In fact, the Prevalent 2023 Third-Party Risk Management Study found that 41 percent of companies experienced an impactful third-party data breach in the last 12 months, and as a result information security teams are increasingly becoming involved in third-party risk management (TPRM) program efforts.
Benefits of Maturing Your Third-Party Risk Management Program
Continually maturing your TPRM program is key to staying on top of ever-evolving third-party risks. Having a mature TPRM program has several benefits:
- Mature programs better protect an organization by ensuring that third-party vendors, suppliers and partners are properly vetted and monitored at the beginning and throughout the business relationship.
- More mature TPRM programs are also more efficient and effective. By building repeatable processes, your organization can assess and monitor risk with fewer manual, ad hoc processes that could result in disruptions, breaches, or fines.
- A mature TPRM program enhances decision making by providing better visibility into third-party relationships. This enables teams to make more informed decisions about who they partner with, the right questions to ask while maintaining those relationships, and when to terminate a relationship.
Despite these clear benefits, building and maturing a TPRM program can appear daunting. To address this challenge, this article:
- Reviews the challenges teams face in building and scaling more mature processes and the types of risks that should be managed
- Defines TPRM program maturity in the context of the Capability Maturity Model, a common framework for measuring maturity
- Examines each stage of the TPRM maturity model and the steps needed to advance to more mature levels
Challenges to Maturing Your Third-Party Risk Management Program
Before defining what a mature TPRM program looks like, consider common challenges faced by organizations that inhibit their maturity.
Maintaining Silos
In many organizations TPRM is owned by the IT security team, but procurement owns the relationship. Other teams throughout the enterprise, such as legal, also typically have input into third-party relationships. If the different teams in your organization do not share data or leverage common processes, then it will be difficult to build and scale your program.
Using Manual Processes
Tracking requirements, vendor responses, and mitigation tasks in spreadsheets or shared documents is prone to errors and data inconsistencies. This approach is also un-auditable if and when changes are made. Most importantly, manual processes simply do not scale. While it may be possible to track a single vendor using a spreadsheet, manually managing hundreds or thousands of vendors is impossible.
Focusing on Onboarding Only
In most cases, third-party risk assessments are conducted prior to onboarding a new vendor. While initial assessments are obviously important, mature TPRM programs include ongoing monitoring of all risk factors across all vendors. After all, risk is not static. It may increase if a vendor has a change of management, sells a line of business, suffers a cybersecurity breach, or fails a regulatory audit. Risk may also decrease with the introduction of a new product or a change to a vendor that improves quality or reduces costs.
No Visibility into Fourth and Nth Parties
Risk extends beyond your direct partners and vendors. Your vendors’ vendors – so-called 4th and Nth parties – can also present risk. Most TPRM programs – particularly manual programs – are incapable of adequately identifying and monitoring these extended parties.
Best Practices for Achieving TPRM Maturity
Our free guide presents a straightforward framework for benchmarking and evolving your TPRM program.

Types of Third-Party Risks Addressed by Mature TPRM Programs
Another challenge that your organization may face on the road to TPRM program maturity is understanding the operational risks that arise when a vendor or supplier cannot meet required Service Level Agreements (SLAs). A more mature program, however, will enable you to discern a broader range of threats and risks, including:
Cyber Risk
Cybersecurity is critical in third-party risk assessments. Ransomware, distributed denial of service (DDoS), and other attacks can shut down your organization, making it impossible for your company to fulfill its business obligations. While the 2020 SolarWinds Breach, in which attackers compromised SolarWinds’ Orion code base to install back doors, was perhaps the most significant cyber breach in recent years, it was by no means the only third-party breach.
- An attack on Latitude Financial Services, a leading Australian personal loans provider, exposed personal information on over 330,000 customers of two of Latitude’s service providers. Exposed data included passports and passport numbers. Attackers breached a vendor to obtain Latitude employee login credentials.
- Customer proprietary network information (CPNI) on over 9 million AT&T wireless customers was stolen after attackers breached a marketing vendor for AT&T.
- The personal data of millions of United Auto Workers retirees was stolen from Benefits administrator NationBenefits – including health plan ID, Medicare information, and Social Security numbers. Attackers exploited a cybersecurity weakness in the file transfer software used by NationBenefits to gain access.
Compliance Risk
Most organizations operate under a myriad of evolving regulatory requirements concerned with protecting sensitive data and systems. Many of these regulations, including HIPAA, the California Consumer Privacy Act (CCPA), the Virginia Consumer Data Protection Act, and Europe’s General Data Protection Regulation (GDPR), require organizations to protect the private information of their consumers, customers and employees. Other regulations concern the protection of non-public financial information. Violations can result in fines and reputational damage.
Financial Risk
Procurement teams must have visibility into the financial stability of their third-party vendors and suppliers, including debts its vendors owe and the credit they extend to customers. A declaration of bankruptcy can result in lost business and supply chain disruptions.
Corporate Social Responsibility
Investor concerns around environmental, social and governance (ESG) practices continue to grow. For example, following Russia’s invasion of Ukraine, doing business with firms affiliated with the Russian government became unpalatable to many companies. Organizations also need to protect themselves against accusations that their supply chain is involved with human rights violations, employing child labor, or causing environmental damage.
Reputational Risk
Adverse media coverage or negative news about a supplier has the potential to harm the reputation of its customers. This can happen when the supplier is involved in unethical hiring practices, quality issues with their products, criminal activities, or environmental disasters.
Webinar: 4 Best Practices for Benchmarking & Auditing Your TPRM Program
In this webinar, audit experts Alastair Parr and Joe Toley share their best practices for auditing your TPRM program's maturity.
Defining TPRM Maturity Using the Capability Maturity Model
In general, less mature programs are characterized by unpredictable or poorly controlled processes, while more mature programs are proactive, predictable, measured and controlled. A maturity model can provide a blueprint for assessing and advancing your organization’s business practices at a point in time and help define a path to greater process maturity. In this paper we leverage the Capability Maturity Model developed by Watts Humphries and others at the Carnegie Mellon University Software Engineering Institute in the late 1980s as a foundation for examining TPRM program maturity.
The Capability Maturity Model recognizes that processes evolve over time, and that as organizations gain experience and knowledge, they can improve their processes to become more efficient, effective and predictable. The maturity model can be applied to any type of organizational process, including software development, project management, quality assurance, or customer support.
The 5 Pillars of TPRM Maturity
The Capability Maturity Model for Third-Party Risk Management examines five key pillars necessary to support the current and ongoing success of a TPRM program. Within each pillar we examine less mature and more mature approaches.
1. Entity Coverage
Most organizations begin their TPRM programs by assessing their most critical vendors. This is a logical approach, but risk can come from any entity. More mature organizations will have a consistent method for tiering or risk-ranking vendors to ensure that all are included in the program, including 4th- and Nth-party vendors.
2. Content
Risk assessment questionnaires often begin as ad hoc initiatives. Questions are given to vendors and free-form answers are received and evaluated. More mature programs will regularly review assessment questions to understand what the question is trying to find in terms of risk to the organization and weight the questions appropriately. More mature programs will also be diligent in ensuring that vendors supply requested evidence of compliance.
3. Roles and Responsibilities
Less mature programs may follow guidelines but lack documentation of procedures and clear roles and responsibilities. Mature programs will train assessment participants and publish and follow an operational manual to ensure that processes are standardized. More mature programs will have documented RACI charts establishing responsible, accountable, consulted and informed individuals throughout the organization.
4. Remediation
Remediation metrics are focused on the efficiencies, standardization, and quality of the risk management approach following the identification of risks. Less mature programs will identify risks and request remediation from vendors. More mature programs implement scoring mechanisms to weight risks and remediations and prescribe standardized remediation guidelines to vendors.
5. Governance
Governance includes how the program is measured and success is proven. Less mature programs lack sufficient assessment reporting and third-party program audits. More mature programs aggregate third-party assessment data to provide teams with the intelligence necessary to measure risk and steer decision making, and measure third-party vendors and suppliers on key performance indicators (KPIs) and key risk indicators (KRIs).
Key Questions to Ask
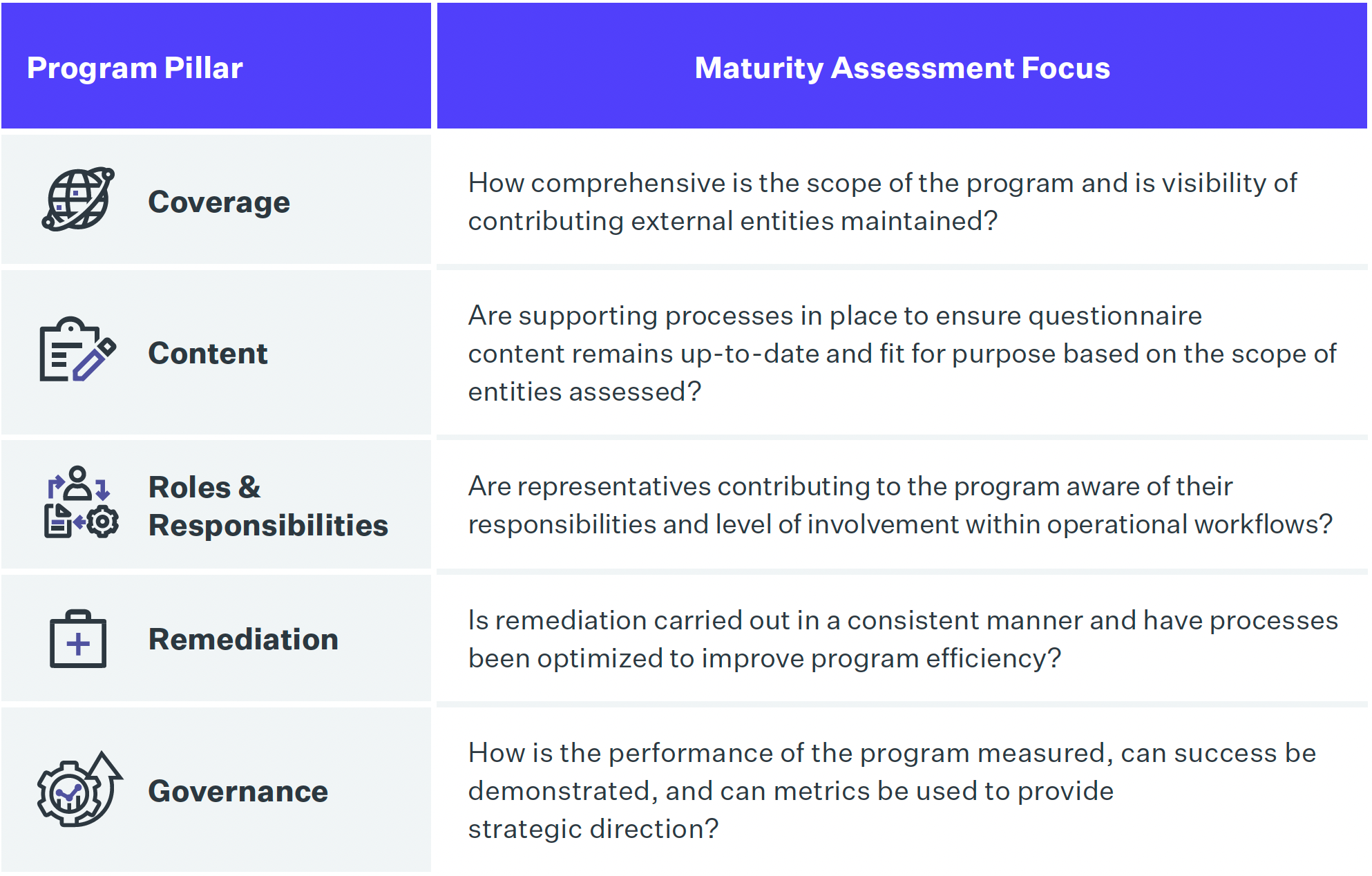
An overview of the program pillars contributing to TPRM maturity.
Third-Party Risk Management Maturity Levels
In the Capability Maturity Model, program maturity in each of the five pillars is ranked across five levels from immature (1) to visionary (5). The scoring is standardized to ensure that all TPRM programs are assessed and scored in a consistent way. This way, you can benchmark a vendor’s maturity score against peers of a similar scale, complexity and vertical. .

The TPRM Capabilities Maturity Model.
Level 1: Immature
Organizations in the first level of the Maturity Model do not prioritize TPRM. Risk management is siloed. Activity is ad hoc and reactive, occurring only when a problem arises or when vendor red flags are obvious. Because processes are undocumented and poorly defined, a successful assessment for a single vendor is unlikely to be repeatable.
TPRM in Level 1 is a manual process for a limited number of vendors. Vendor questionnaires are inconsistent and distributed as discrete spreadsheets. Responses may be in narrative form and difficult to assess for risk. Standards for risk mitigation controls do not exist. Teams do not monitor vendors for ongoing compliance or new risks.
Requirements to advance to Level 2: In Level 1, organizations have not committed themselves to understanding or measuring third-party risk. Nascent teams have not defined and documented processes to enable them to be replicated. Advancing to Level 2 requires additional discipline to define policies and processes to achieve consistency between assessments.
Level 2: Developing
In Level 2, some (but not all) teams have defined and documented processes that allow for repeatable results. For example, security teams may have standardized questionnaires and penetration testing requirements, or finance may have standardized financial disclosure parameters. Other teams, however, remain ad hoc. This siloed approach leads to inconsistent assessments and prevents programs from scaling.
Without a standardized approach, vendors can not be tiered according to their risk levels. This leads to higher risk if critical vendors are lightly assessed and inefficiencies if low risk vendors are over-scrutinized. Level 2 organizations continue to use spreadsheets and shared documents, making reliable, auditable, and thorough TPRM unattainable.
Requirements to advance to Level 3: Level 2 organizations lack information, documentation and consistency. They require executive support to define TPRM requirements across all functions and a means for reporting on risks and mitigations. Achieving a scalable program requires automation.
Level 3: Scalable
At Level 3, TPRM has been properly resourced and processes are consistent within individual functions in an organization. Most silos have been dismantled and teams have standardized, documented, and integrated activities for identifying and evaluating risk. Risk monitoring has expanded beyond business and IT risk to include corporate governance, compliance, and reputational risk. Risk tiering
is standardized, and organizations begin to institute contract lifecycle management and formal offboarding procedures.
Processes at Level 3 are semi-automated. For example, onboarding may leverage automated questionnaires, while monitoring for remediation and ongoing compliance with requirements remains manual. This enables teams to moderately scale TPRM but can still leave gaps in visibility.
Requirements to advance to Level 4: Standardized processes, reporting and automation are required across all departments. Reporting at Level 3 is typically done by individual departments. To advance, organizations should focus on eliminating silos and institute centralized reporting.
Level 4: Optimized
Level 4 organizations view TPRM as a strategic requirement and have standardized policies and procedures across all departments. TPRM teams perform automated, standardized vendor risk assessment with vendor risk monitoring, assessment workflow, and remediation management across the entire vendor life cycle. Risk mitigation controls are formalized, and vendor monitoring is fully implemented. Automation also enables the program to be fully auditable.
Level 4 organizations can scale TPRM to all vendors across the entire vendor lifecycle. Reporting on KPIs and KRIs is automated and continuous improvement initiatives are data-driven. Communications with third parties focus on mutual benefits of a TPRM program.
Requirements to advance to Level 5: Institutionalize a program to examine each part of the TPRM program to make incremental improvements over time. Reexamine IT and non-IT risks and mitigation strategies at least annually.
Level 5: Visionary
Level 5 is an aspirational level of maturity achievable by few organizations. It represents a fully automated TPRM program that anticipates risks, assigns effective controls, and monitors vendors for cyber, operational, financial, environmental, compliance, reputational, ESG and performance risk. A visionary organization works with vendors proactively to improve the vendor’s business while lowering risk.
At level 5, residual risk remains but can be addressed quickly, when necessary, through formal, tested procedures, and then accepted by the business.

TPRM maturity criteria by pillar and level.
The Next Step in Your TPRM Program Maturity Journey: Take the Free Assessment
A mature TPRM program can help identify and mitigate potential risks associated with third-party relationships, reducing the likelihood of negative impacts on the organization. Anticipating third party risk helps organizations avoid costly disruptions as well as financial and reputational damage. By automating risk identification and controls, and integrating the needs of all stakeholders, a mature TPRM program provides organizations with more accurate and comprehensive information on third-party relationships, enabling better decision-making.
Calculate Your TPRM Program Maturity
Whether you are just starting your third-party risk management program or working to mature an existing program, Prevalent can help. Prevalent automates third-party risk management using a single platform to collect third-party risk information, quantify risks, recommend remediations, and provide reporting templates. The Prevalent Platform includes a library of over 750 standardized assessments, customization capabilities, continuous risk monitoring, and built-in workflow and remediation.
To identify where you are in your TPRM program maturity using the Capability Maturity Model continuum, request a free program maturity assessment today.
Free TPRM Maturity Assessment
Work with Prevalent experts to get in-depth report on the state of your current TPRM program, plus practical recommendations for how to bring it to the next level.

-

The Top 7 TPRM Predictions for 2025
2025 promises to be a consequential year for third-party risk management. Read our top TPRM predictions...
12/12/2024
-

Developing a Third-Party Risk Management Policy: Best Practice Guide
Learn how a third-party risk management (TPRM) policy can protect your organization from vendor-related risks.
11/08/2024
-

Vendor Offboarding: A Checklist for Reducing Risk and Simplifying the...
Follow these 7 steps for more secure and efficient offboarding when third-party relationships are terminated.
10/17/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




