Supplier Risk Management: The Definitive Guide

What Is Supplier Risk Management?
Supplier Risk Management (SRM) is the practice of identifying, analyzing, and addressing the risks that may arise from working with third-party suppliers. These risks include data breaches, operational failures, and other business disruptions that may affect an organization’s suppliers – and therefore limit its ability to deliver products and services to its customers.
A supply chain is broadly defined as the sequence of processes required to produce a product or commodity. These sequences can range from short and simple, such as a farmer selling goods at a farmer’s market, to long and complex, such as a consumer products company that designs and markets its products but relies on hundreds of third, fourth, and Nth parties for raw materials, assembly, packaging, and distribution.
The goal of SRM is to maintain supply chain continuity in the event of an incident that could negatively impact business relationships, customer service, and profitability. Effective SRM programs prioritize interdependent risks that can lead to supply chain disruptions and downtime through supplier assessments, continuous monitoring, data analysis, and risk mapping. Well-designed programs also include risk mitigation and risk transfer processes, as well as the ability to measure and analyze key performance indicators (KPIs) for ongoing program optimization.
Gaining a clear understanding of supplier risk enables the organization to better prepare for and respond to disruptions to product and service delivery. Additionally, planning can help organizations implement automated supplier risk management solutions to shoulder part of the load.
Why Supplier Risk Management Is Critical Today
Today, supplier risk management means the difference between success and failure for many organizations. The COVID-19 pandemic, geopolitical unrest, climate change, natural disasters, and other events have spurred many companies to revisit their approaches to SRM. While just-in-time supply chains and global outsourcing reduced costs and increased efficiency during times of stability, these practices have left supply chains exposed to existential threats in recent years.
While you may be unable to predict specific disruptions, a comprehensive and effective supplier risk management program will help your organization prepare for unexpected events. It also addresses board-level topics, such as operational resilience, business continuity, and product lifecycle management.
The Supply Chain Resilience Toolkit
Based on ISO 22301 standard practices, the Supply Chain Resilience Toolkit provides instant access to expert guidance, customizable templates, and structured worksheets.

Types and Examples of Supplier Risks

Cybersecurity Risks
Some of the most important risks facing 21st-century supply chains are data breaches and other cyber incidents, which can jeopardize suppliers, their customers, and even their customers’ customers. In many cases, large enterprises will have robust cybersecurity programs, but these don’t always extend to third-party organizations that may have substantially less cybersecurity knowledge and capability. For example, in 2013 Target suffered a massive data breach that exposed the PII of up to 40 million consumers. The attackers’ point of entry was an HVAC subcontractor who had served numerous Target locations.

The SolarWinds Breach
Another prominent example is the 2020 SolarWinds attack, which compromised the company’s Orion Platform. This was one of the most far-reaching and sophisticated cyber-attacks seen in recent history. The SolarWinds supply chain breach has wreaked havoc on Orion consumers around the world despite their best efforts to recognize and minimize the risks. In fact, one study found that the average cost to companies affected by the SolarWinds attack was about $12M.
Prevalent found that 37% of impacted parties had no documented incident management policy for responding to the SolarWinds breach. This intrusion caught many organizations off guard, revealing internal procedure deficiencies regarding customer reporting and a lack of appropriate incident response planning.

The SolarWinds breach is a salient example of how organizations can suffer cascading effects from supply chain cybersecurity risks. Even if an organization's direct suppliers didn’t use SolarWinds, their subcontractors may have. This is also an example of fourth-party risk, where the cybersecurity shortfalls of unknown subcontractors could negatively impact an existing (and even carefully managed) supply chain. These risks underscore the importance of gaining a detailed and complete understanding of your supply chain, including subcontractors, accurately accounting for potential risks, and proactively creating an incident response plan for when events occur.
Compliance Risks
Recent disruptions in global supply chains have increased the focus on SRM not only at the board level but also among regulators and legislators. While several regulations include requirements governing supplier IT security risk, most organizations base their compliance programs on best practices outlined by either NIST or ISO.
NIST
Organizations handling U.S. government information are required to adhere to guidelines from NIST or the National Institute of Standards and Technology. Because NIST publishes resources for managing risks applicable to any company, nearly 50% of private sector organizations have also adopted their guidelines. Several NIST special publications outline controls that address supplier IT security, including SP 800-53, SP 800-161, and the NIST Cybersecurity Framework.
ISO
The International Organization for Standardization (ISO) is a body of experts that develops voluntary, consensus-based standards to solve global challenges. ISO information security management standards fall under the ISO 2700 family, with ISO 27001 and ISO 27002 being the most widely known. Section 15 of ISO 27001 and ISO 27002 summarizes the requirements for securely dealing with various types of third parties. This is in addition to ISO 270036-2, which focuses specifically on information security requirements for supplier and acquirer relationships.
Regulations Outside of IT Security
IT security isn’t the only category of compliance risk when it comes to supplier relationships. For instance, several examples of ESG regulations require oversight of supplier practices spanning climate change and sustainability (E), social justice, pay equity, worker protections (S), governance, anti-bribery and corruption, and diversity (G).
Business & Financial Risks
Business supply chain risks can take many forms. For instance, a key supplier could declare bankruptcy and be unable to deliver on its contracts. In fact, some studies show that 25% of businesses have been affected by a supplier's financial failure in the past year.

Mergers and acquisitions can also signal a change in strategy or market consolidation that could impact service delivery, prices, or contract terms. In addition, leadership turnover or legal trouble can impact an organization’s culture, strategy, and ability to execute against goals.
Organizations are also increasingly subject to regulatory penalties for financial disclosures and ethics. For example, the Office of the Comptroller of the Currency (OCC) provides specific guidance for banks entering relationships with third parties such as cloud service providers, data aggregators, fintech companies, and subcontractors.
When evaluating potential vendors, it is critical to understand the organization's financial situation, existing contractual obligations, and other factors that could prevent them from effectively executing your contract. The less due diligence that is performed before onboarding a vendor, the more likely you are to experience a significant business disruption.
Having a formal and documented third-party risk management strategy can help manage these risks. Vendors should be evaluated uniformly based on a predetermined set of metrics that make it easy to compare competing vendors and identify potential suppliers that may have difficulty fulfilling their contractual obligations.
Event Risks
Globalization has made supply chains dramatically more complex. For instance, a natural disaster such as a hurricane, wildfire, earthquake, or tsunami in one country can impact supply chains around the globe. The risk of experiencing supply chain disruptions due to natural disasters is projected to increase due to climate change.
A change in the political conditions or security situation in a key supplier's country can also cause negative supply shocks. Examples include conflicts such as war, changes in tax policy, internal stability issues, and trade embargoes. It’s therefore critical to monitor the political, social, and economic conditions in supplier regions and analyze their potential impacts on your supply chain. Visibility into Office of Foreign Assets Control (OFAC) violations, state-owned enterprises, and politically exposed persons (PEPs) are key to understanding geopolitical risks.
Here are a few significant examples of event risks:

The COVID-19 Pandemic
The COVID-19 pandemic serves as a prime example of how a health crisis can disrupt supply chains on a global scale. In January and February of 2020, China was at the center of the COVID-19 crisis, spurring widespread supply chain breakdowns that were exacerbated by drastic changes in demand for certain products. For instance, supply chains were disrupted for key personal protective equipment such as N95 respiratory masks and face shields while demand skyrocketed. Disruptions spread to consumer goods supply lines as the pandemic progressed, and new variants triggered additional global lockdowns.
The War in Ukraine
The 2022 invasion of Ukraine by Russia forced several global manufacturers to pause production and threatened the global wheat supply. Companies such as Carlsberg, Coca-Cola, Mondelez International, Nestle, and steel manufacturer and miner ArcelorMittal have thus far suspended operations. Ukraine is also a top producer of rare earth metals such as copper, which is an important input to many manufactured goods and electronics. These disruptions have required companies to gather information from suppliers with Ukrainian operations and adjust their production schedules and processes accordingly.
Sanctions are an additional consideration. In the example of the Russian invasion of Ukraine, several nations placed export blocks and sanctions on the Russian government, which have impacted the ability of Russian companies to conduct international business. In response, experts predict an increase in Russian cyber-attacks against Western governments and Western-based companies.
The Suez Canal Obstruction
Another recent example of an unanticipated supply chain disruption is when the Suez Canal was blocked by a giant container ship for 6 days in March 2021, leading to an estimated $9.6 billion dollars of trade held up per day.
It’s impossible to predict pandemics, wars, or disasters far in advance, but it is possible to mitigate the risk and dampen its impact on your organization. In addition to having a plan, organizations can also run simulations on their supply chains. These simulations can help you understand the most vulnerable parts of your supply chain and how natural disasters would affect business operations.
Corporate Social Responsibility and ESG Risks
The concept of being a “good corporate citizen” has been around for a while but is evolving as awareness increases. At one time, organizations could meet the definition of corporate social responsibility (CSR) by giving back to the community through donations of time and money. However, CSR is increasingly associated with environmental, social, and governance (ESG) practices. These include your company’s approaches to environmental sustainability, its relationships with customers, employees, and communities, and how it deals with executive pay, internal controls, and shareholder rights.
In addition, a growing issue in several industries is the use of slave and child labor – for example:
- The plight of the Uyghur minority has put pressure on organizations manufacturing products in China. A 2020 report named 83 global brands using forced labor factories in China, including Nike, Gap, Target, Apple, and H&M. In addition to growing pressure for a consumer boycott of the brands, in 2021, Congress passed the Uyghur Forced Labor Prevention Act to block the import of goods linked to forced labor in China.
- News reports of child labor being used in mining for cobalt used in batteries brought focus to the supply chain practices of Apple, Microsoft, Tesla, Samsung, and others. In addition to reputational damage, several of the companies faced lawsuits for their practices.
- In March 2024, a parts manufacturer in Tennessee, which supplies major companies like John Deere and Yamaha, was mandated to surrender $1.5 million in profits after the Department of Labor discovered that children were employed in hazardous jobs. Additionally, the company was fined $296,951 for subjecting "10 children to oppressive child labor," according to the department.
Regulatory pressure is also growing. The U.S. Securities and Exchange Commission (SEC) recently adopted amendments that will require “certain climate-related information in their registration statements and annual reports,” including “upstream and downstream value chains.” The European Union (EU) Parliament presented mandates that EU businesses “identify and, where necessary, prevent, end or mitigate adverse impacts of their activities on human rights, such as child labour and exploitation of workers, and on the environment, for example pollution and biodiversity loss.”
Capacity Risks
Whether driven by business events, economic conditions, or natural disasters, suppliers may not be able to meet their delivery schedules. That’s why it’s important to continuously measure supplier capacity, including tracking current order status, performance against order history, supplier responses, and acknowledgments. A proactive view of supplier capacity can help your organization be more agile when a disruption occurs.
Performance Risks
Closely related to capacity risks is measuring supplier performance risks, also called key performance indicators (KPIs), which can include quality metrics, on-time delivery performance, and other risks to meeting agreed-upon service levels. Critical to managing supplier performance is a clear dashboard to provide enterprise-level visibility, and setting contractual clauses with enforceable service level agreements (SLAs).
6 Strategies to Reduce Supplier Reputational Risk
Discover which reputational risks to watch out for, what penalties to avoid, and how to automate and simplify your reputational risk management initiatives.

Industry-Specific Supplier Risk Management Concerns
Each industry faces unique challenges in dealing with third, fourth, and Nth party suppliers. It’s critical to account for factors specific to your industry, as well as to conduct regular, detailed reviews to ascertain whether industry changes may jeopardize your supply chain.

Healthcare SRM Concerns
The COVID-19 pandemic laid bare many inadequacies in the U.S. healthcare supply chain. Shortages of personal protective equipment (PPE) and other critical medical devices lasted for months. Healthcare faces many unique supply chain risks due to the unpredictable nature of health crises and the global scope of demand-induced supply chain crunches.
U.S.-based healthcare organizations also need to pay particular attention to data privacy laws and supply chain cybersecurity. In many cases, third-party suppliers will be required to adhere to the same cybersecurity standards as the healthcare organization under regulations such as HIPAA’s “business associate” clause. For additional information on enhancing SRM throughout the healthcare supply chain, we recommend reviewing HHS's HPH Cyber Supply Chain Risk Management (C-SCRM) slide presentation.
Manufacturing & Retail SRM Issues
Manufacturing and retail organizations need to pay close attention to society’s increasing focus on ESG (Environment, Social, Governance) practices. Investors and governments are increasingly scrutinizing the way manufacturers and retailers source their materials – not only through third parties but also through the extended supply chain of fourth and Nth parties.
ESG compliance requirements such as the European Corporate Due Diligence Directive create mandates to affirmatively examine the supply chain for slave labor and other immoral practices, and fines for non-compliance can be heavy. We recommend that manufacturing and retail organizations proactively ensure that ESG is considered in every step of the vendor risk management lifecycle for compliance, ethical, and reputational reasons. Regulations will undoubtedly be tightening in this area, so having a proactive ESG approach will undoubtedly reduce future challenges for your organization.
IT Services, Software & Supply Chain Cybersecurity
At first glance, IT services and software organizations may not be subjected to the same levels of supplier risk as other companies in other industries. Most software companies don’t need to source products and raw materials from politically unstable countries, and most don’t have to worry as much about natural disasters affecting third-party suppliers. However, they are at significant risk from cyberattacks.
In recent years, malicious actors have increasingly resorted to compromising third parties of software and IT companies to distribute malware and damage customers. These attacks illustrate the critical importance for IT firms and other companies to rigorously evaluate the information security practices of third-party software vendors and other organizations with access to sensitive IT infrastructure.
These issues are particularly acute for MSPs and other IT service providers with customers across multiple verticals. For instance, the 2021 Kaseya breach exploited a vulnerability in a solution used by managed service providers (MSPs). The exploit, in turn, enabled the attackers to distribute ransomware to MSP customers using the Kaseya solution.
The Top 15 NIST Supply Chain Risk Management Controls
Discover how you can use NIST SP 800-53 as a foundation for building a more robust supply chain risk management program.

Understanding Profiled, Inherent & Residual Risk in the Supply Chain
Supplier risk can be broadly classified into three buckets - inherent risk, profiled risk, and residual risk. Understanding these categories of risk will enable you to effectively prioritize resources and mitigate risk throughout the extended supply chain.

Profiled Supplier Risk
Profiled risk accounts for risks based on the services provided by the supplier, the types of data and systems that they have access to, and the industry that they operate in. For example, if a manufacturing organization sources 90% of its raw materials from a single supplier in a politically unstable country, then the supplier would have a high profiled risk. Conversely a supplier of a single, minor, easily replaceable component would have a low profiled risk. When considering supplier-profiled risks, you need to account for:
- Compliance requirements: Upcoming such as the European Corporate Due Diligence Draft Directive are likely to impose heavy fines on organizations that fail to incorporate ESG best practices into the supply chain. Suppliers with a high likelihood of ESG concerns, or with a poor track record of managing ESG, represent a higher profiled risk.
- Data & IT access: A third-party supplier’s profiled risk directly correlates with the scope and type of data and IT systems they have access to. Organizations with high levels of access to confidential information access have a higher profiled risk. If a supplier stores, processes, or interacts with your corporate data, then their security program is effectively your security program.
- Location: Organizations that operate in politically unstable environments represent a higher profiled risk than organizations that don’t. Political instability can quickly disrupt supply chains, compromise sensitive data, and lead to other difficult-to-predict adverse outcomes.
Supplier risk managers need to consider many factors when gauging the profiled risk of potential suppliers. Don’t make the mistake of skipping the profiled risk step, as it provides critical context for selecting questionnaires for each vendor tier in your third-party ecosystem. Without an understanding of profiled risk, you’ll inevitably ask the wrong questions, get irrelevant data, and end up with inaccurate inherent risk scores.
Inherent Supplier Risk
Inherent risk indicates a vendor’s risk level before accounting for any specific controls required by your organization. For example, if a healthcare organization is looking at data analytics companies to help them process patient data, a company without documentation demonstrating HIPAA compliant policies would represent an unacceptably high inherent risk. The hospital would have the choice of requiring the vendor to implement HIPAA-compliant policies and procedures or walk away from the contract. When analyzing a potential vendor’s inherent risk, consider the following:
- If the vendor suffered a major cyberattack that left them unable to perform against their contract, would your supply chain experience a major disruption?
- Does the vendor currently meet all compliance requirements that would flow down from your organization? (e.g., HIPAA, CCPA, GDPR)
- Does the vendor have its own supplier risk management program that enables it to continue delivering in the event of fourth- or Nth-party disruption?
- Does the potential supplier have an ESG compliance program in place? Do they evaluate fourth and Nth parties for bribery, corruption, modern slavery and other ESG risks?
Asking these and other relevant questions can help you discern the inherent risk that a potential supplier poses to your organization and its supply chain. Getting responses to these questions will enable you to draft a detailed set of requirements for a vendor based on a combination of their profiled and inherent risk.
Residual Supplier Risk
Residual risk is the risk that remains after a vendor has successfully implemented controls required by your organization. Regardless of the vendor’s profiled risk, inherent risk, and remediation activities, some residual risk will always be left over. The goal of an effective supplier risk management program is to bring residual risk to a level that your organization can tolerate across its extended supply chain.
To achieve an acceptable level of residual risk, you will need to ensure that all suppliers have achieved your organization’s “must-have” requirements to ensure secure and compliant supply chains. These requirements may include:
- Robust and documented information security programs
- Extensive disaster recovery planning
- Visibility into fourth and Nth parties
- An ESG compliance program
- Visibility into raw material sourcing (e.g., conflict minerals)
Keep in mind that residual risk is not static throughout the supplier risk management lifecycle. It is critical to monitor third parties through the lifecycle of the contract in order to stay on top of changes in residual risk resulting from organizational or environmental changes
A Supplier Risk Management Strategy Outline
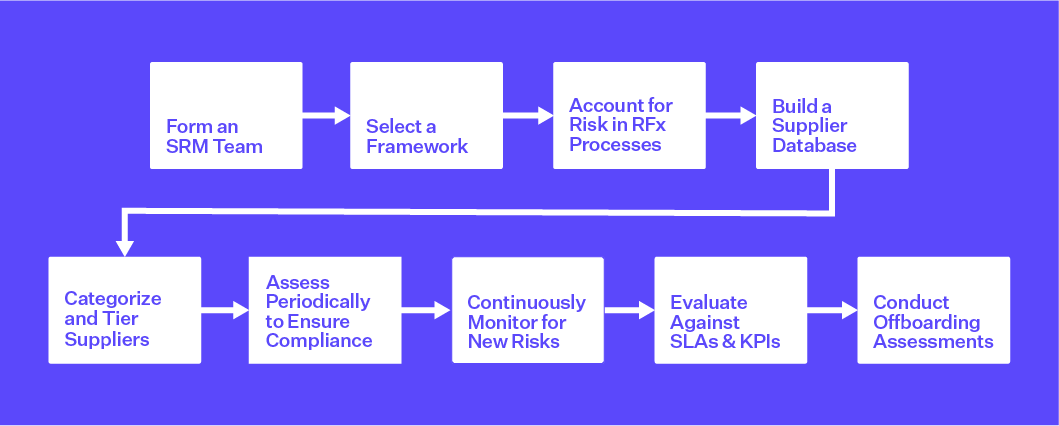
1. Form a Cross-Departmental SRM Team
Identifying and quantifying supplier risk can be daunting at first glance, so it is essential to have the right team for management and governance over your SRM program. Participants can include representatives from procurement and sourcing, risk management, security and IT, legal and compliance, and data privacy teams. It is also critical to engage with product management and manufacturing to understand the potential risks at each node in the value chain.
2. Select a Risk Management Framework
Basing your SRM program on a risk management framework can give you a foundation of best practices and guidance. Many organizations align to either NIST or ISO frameworks, depending on their industry and other factors. Specific NIST guidelines to consider include NIST CSF v2.0, NIST SP 800-53, and NIST SP 800-161. For ISO standards, start with ISO 27001 and ISO 27036-2.
3. Account for Risk in RFx Processes with Pre-Contract Due Diligence
When evaluating new suppliers, be sure that RFP, RFI, and other RFx processes include information gathering on business, financial, and reputational risk from sources including:
- Business news (e.g., M&A activity, regulatory and legal actions, operational changes, and leadership changes)
- Adverse media coverage (e.g., ESG violations, modern slavery, bribery, corruption)
- Data breach lists
- Financial records
- Sanctions lists (e.g., OFAC, EU, UN, BOE, FBI, BIS, etc.)
- Global enforcement lists and court filings (e.g., FDA, US HHS, UK FSA, SEC, etc.)
- State-owned enterprise lists
- Politically exposed persons (PEP) lists
Risk intelligence networks and risk profiling services can help to automate this process. When new suppliers are selected, be sure to have a sound contract lifecycle management process in place to streamline and secure the process.
4. Centralize Visibility Over Supplier Profiles
Building and maintaining a centralized supplier database is essential to ensuring an effective SRM program. The database should include comprehensive supplier profiles and provide role-based access to company contacts, demographics, 4th-party and Nth-party connections, and risk intelligence – starting with any profiled risk data and external risk information captured during the sourcing and selection stage.
5. Categorize and Tier Suppliers Based on Inherent Risk
To ensure SRM program effectiveness and make the best use of limited resources, you will want to categorize and tier your suppliers based on their inherent risk. As discussed earlier, inherent risk is a supplier’s risk before accounting for any specific controls required by your organization. Effective inherent risk scoring (see chart below) can combine inputs from simple internal questionnaires as well as from any external risk data gathered during the sourcing phase.

A simple SRM risk scoring chart
6. Conduct Periodic Risk Assessments to Ensure Compliance
Once your suppliers are profiled, categorized, and tiered, it should be easy to determine the frequency and scope of future risk assessments for each category of supplier. For instance, you may conduct annual assessments of critical suppliers based on industry standards, regulatory mandates, or unique organizational requirements. Assessments may request information about internal security controls, business continuity plans, disaster recovery plans, and more. For more details on assessment types, review our blog post, How to Select a Vendor Risk Assessment Questionnaire.
7. Continuously Monitor for New Supplier Risks
Supplier risks are constantly emerging in response to the rapidly shifting economic, geopolitical, and cybersecurity environment. It’s therefore important to continuously monitor your critical suppliers for new business, financial, reputation, and cyber risks. This intelligence can be used to adjust supplier risk scores and trigger response, mitigation, and remediation activities – such as sourcing new suppliers, altering shipping routes, or requiring further assessments.
8. Ensure Adherence to SLA and Performance Requirements
Many of the assessment and monitoring mechanisms discussed in this post can also be customized to evaluate supplier performance against SLAs and other contract requirements. Start by establishing supplier key performance indicators (KPIs) and assign thresholds and owners for each KPI based on the contract’s attributes. An automated platform can trigger alerts when KPIs are missed or when key risk indicators (KRIs) are exceeded.
9. Protect Against Risks When Supplier Contracts End
Offboarding is often overlooked in supplier risk management, so security risks are often heightened after a contract ends. That’s why it’s critical to review the profiles of suppliers being terminated and conduct offboarding assessments. These assessments can be used to validate that final contract terms are met, deliveries are made, IT and/or physical access is revoked, assets are returned, and sensitive data is destroyed. Here’s an offboarding checklist to get you started.
Supplier Risk Management Strategy Explained
Discover nine key steps to implementing a successful SRM program.
Tips for Your SRM Program
Acknowledge that Supplier Risk Doesn’t Stop at Third Parties
An organization's risk is not limited to its direct (third-party) associates and suppliers. Harm may also be introduced by their partners, also known as "fourth parties," as well as those deeper in the supply chain. The challenge of recognizing such organizations, the associated risks posed by third parties, and their ability to administer and implement controls against those risks is of great concern for businesses today. The complexity involved in assessing and responding to these types of risks requires a robust and comprehensive Third-Party Risk Management Program.
Create Incident Response Plans for Major Suppliers
No matter how strong your SRM and procurement programs are, problems will occur. For particularly critical portions of your supply chain, take the time to map out contingency plans that can enable you to rapidly transition in the event of an incident. This can mean the difference between widespread disruptions across your organization or a minor hiccup in operations. The more important the supplier is, the more critical it is that you map out specific and actionable incident response plans.
Implement an SRM Training Program
For larger organizations, it can be extraordinarily difficult to ensure secure and robust supply chains across the enterprise. Various departments may have separate systems for sourcing and selecting vendors, so it can be challenging to identify and track all third-party suppliers (and their supply chains, in turn).
An SRM training program can help align decision-makers throughout the organization and provide clear standards for how individuals and departments should onboard, monitor, manage, and offboard third parties. Without clear standards that have been adequately communicated uniformly, an SRM program can quickly be derailed.
Next Steps
Wondering how to get started? Learn more about our solutions for supplier risk management, our supplier risk monitoring service, and our procurement due diligence service. Interested in whether Prevalent solutions and services may be a fit for your organization? Request a demo.
-

Vendor Due Diligence Strategy and Checklist
With a mature vendor due diligence strategy, businesses can assess risks early, categorize vendors accordingly, and...
01/16/2025
-

Vendor Offboarding: A Checklist for Reducing Risk and Simplifying the...
Follow these 7 steps for more secure and efficient offboarding when third-party relationships are terminated.
10/17/2024
-

Supplier Compliance: Key Regulations to Consider for Your SRM Program
Organizations are increasingly being held accountable for compliance in their supply chains. Be sure to review...
07/25/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




