Risk Monitoring Strategies and Sources for Vendor Managers

Risk monitoring is the practice of collecting and analyzing externally available data to assess potential threats and impacts. For vendor managers, identifying risks starts with proactively watching feeds of cyber threats, business news, and financial data. This intelligence can be used to identify breaches, compliance violations, supply chain disruptions, and other threats to the business relationship.
This blog answers questions including:
- Why should vendor managers validate assessments with monitoring?
- Which information sources should vendor managers monitor?
- How can you avoid falling into a major monitoring trap?
Why Vendor Managers Should Validate Assessments with Risk Monitoring
Vendor managers often use continuous, external cyber and business risk monitoring to validate vendor assessment responses. Although periodic, internal control-based assessments reveal how vendors govern IT security and privacy, a lot can happen in the year between assessments!
Continuously monitoring your vendors has several benefits, including:
- Immediacy – Gaining an instant view of public exposures can inform your tiering and prioritization logic when onboarding vendors.
- Validation – Validating if responses to internal vendor surveys are consistent with external cyber, business and financial events affecting their organizations.
- Frequency – Obtaining frequent, unbiased insights into a potential vulnerabilities or relevant business risks that can negatively impact your business.
Risk monitoring makes vendor risk management more holistic.
Which Cyber Information Sources Vendor Managers Should Monitor
Vendor risk monitoring involves more than simply scanning for cybersecurity vulnerabilities. It should also include information from multiple external sources of cyber threat intelligence, including:
- Internet sensor networks
- Global threat databases
- Collaborating security partners
- Anti-virus users
This intelligence can help you better understand risks to your vendor’s public-facing assets.
Common sources of vendor risk data are listed below.
| Cyber Risk Monitoring Target | Description |
|---|---|
|
Dark web |
Recent, frequent mentions of a company on the Dark Web often correlate with threat activity against the company. Attention on Dark Web markets may also indicate illicit sales of company assets or accounts, or fraud schemes. |
|
Domain abuse/Typosquatting |
New domain registrations similar to existing corporate domains can be indicators of potential domain abuse (such as phishing). They can also indicate efforts to prevent or mitigate domain abuse. |
|
Email security |
Sender policy framework (SPF) policy configurations, domain keys identified mail (DKIM), and domain-based message authentication, reporting and conformance (DMARC) |
|
Leaked credentials |
Exposed credentials and emails can indicate password or corporate email address reuse by company employees. This also raises the risk of credential stuffing attacks and targeting by attackers. |
|
Incidents |
Security breach disclosures and validated cyber-attacks reports can point to recent attacks, breaches, or other events that jeopardize information assets. |
|
Infrastructure |
IT policy violations, abuse of company infrastructure, infections in company infrastructure, malware, misconfigurations, vulnerabilities, infected hosts, unsupported software |
|
Web application security |
SSL/TLS certificates and configurations |
This information is exactly what is visible to hackers. The intelligence can be used to help vendors scrub their open-source footprints or close security gaps in their processes. This is similar to cleaning up your credit report prior to applying for a home loan.
Which Business Intelligence Sources Vendor Managers Should Monitor
The next area that vendor managers should monitor is qualitative business information that can indicate possible future risks. Business risk indicators include the following:
- Operational risks – M&A activity, layoffs, leadership changes, partnership changes, customer relationships, and geographic expansions can all disrupt an organization’s operations.
- Brand risks – Data breaches, product recalls, and brand changes can negatively impact public perception. This can lead to unforeseen costs or cuts to business operations.
- Regulatory/Legal risks – Probes, fines, economic sanctions/blacklists, and major lawsuits and settlements create distractions and can inhibit operations.
Which Financial Sources Vendor Managers Should Monitor
Vendor managers should monitor financial indicators such as bankruptcies, capital transactions, and data breach impacts on financial viability. This can also help procurement teams pre-screen new vendors, monitor existing vendors, and evaluate financial and organizational health. This results in sourcing decisions that are faster and better informed.
Together, cybersecurity, business risk and financial monitoring provide a much more comprehensive view of a vendor. This "outside-in” view gives you an edge in interpreting the potential impact of vendor risk. It also augments “inside-out” assessments to deliver a more informed and accurate risk score.
Ask These Questions to Avoid This Monitoring Trap
Some companies can fall into the trap of thinking that monitoring alone will suffice as a vendor risk management strategy. Consider whether a “score” or “security rating” will really address the vendor risk management challenges you face.
Security ratings tools only provide an external network scan showing basic cyber risks. With no vendor assurance and no context scoring, rating vendors provide a limited view of vendor risk. This means there is no real assessment happening.
To determine whether or not your current solution is meeting your monitoring and vendor risk management needs, consider these questions:
- What about measuring a vendor’s internal adherence to compliance mandates? Can an external scan reveal that?
- Can a security score tell you how a vendor handles your data?
- How can security ratings automate the collection of vendor evidence and due diligence?
While outside-in risk scoring or ranking can deliver risk insights, it cannot meet compliance requirements on its own. Best practices as published by Gartner and others recommend combining vendor assessments with continuous monitoring for more complete vendor risk management.
Next Steps
Vendor managers should cast a wide net in third-party risk monitoring. With the right sources, combined with internal assessment results, you can gain a more complete picture of your vendors’ risks.
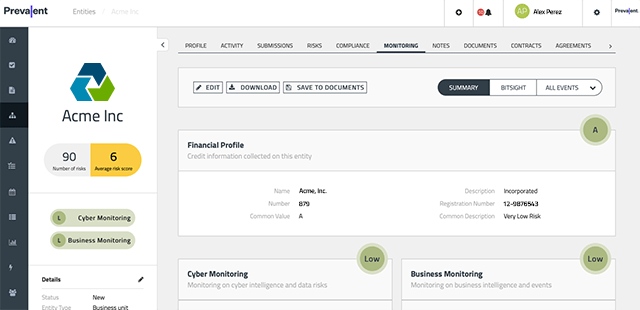
Prevalent Vendor Threat Monitor delivers business, cyber and financial intelligence from 500k+ sources.
Learn about our proven, 5-step approach to vendor risk management in our best practices guide, or request a demonstration today.
-

Third-Party Risk Management: The Definitive Guide
Third-Party Risk Management (TPRM) has advanced from being an annual checklist exercise to a critical daily...
01/23/2025
-

Vendor Due Diligence Strategy and Checklist
With a mature vendor due diligence strategy, businesses can assess risks early, categorize vendors accordingly, and...
01/16/2025
-

The Top 7 TPRM Predictions for 2025
2025 promises to be a consequential year for third-party risk management. Read our top TPRM predictions...
12/12/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




