Interagency Guidance on Third-Party Relationships: How to Comply

On June 6, 2023, the Board of Governors of the Federal Reserve System (the Board), the Federal Deposit Insurance Corporation (FDIC), and the Office of the Comptroller of the Currency (OCC) issued uniform guidance on managing risks associated with third-party relationships in banking organizations. Interagency Guidance on Third-Party Relationships: Risk Management is based on the OCC’s 2013 guidance and 2020 FAQs. It replaces each agency’s existing guidance on third-party relationships and applies to all banking organizations supervised by the agencies.
With full compliance expected with 12 months, now is the time for regulated banks to review the recommendations and determine how their third-party risk management programs are impacted. This post examines the goals of the Guidance and offers best practices for achieving compliance.
The Goal of the Interagency Guidance on Third-Party Relationships
The goal of the Interagency Guidance is to bring uniformity and consistency to how banking organizations develop and enforce risk management principles as they relate to third-party relationships. According to the document, "the final guidance offers the agencies’ views on sound risk management principles for banking organizations when developing and implementing risk management practices for all stages in the life cycle of third-party relationships."
Third Party Definition and Principles in the Interagency Guidance
The Guidance defines a third-party relationship as “any business arrangement between a banking organization and another entity, by contract or otherwise;” describes the third-party risk management life cycle; and identifies principles applicable to each stage of the third-party life cycle as depicted below:
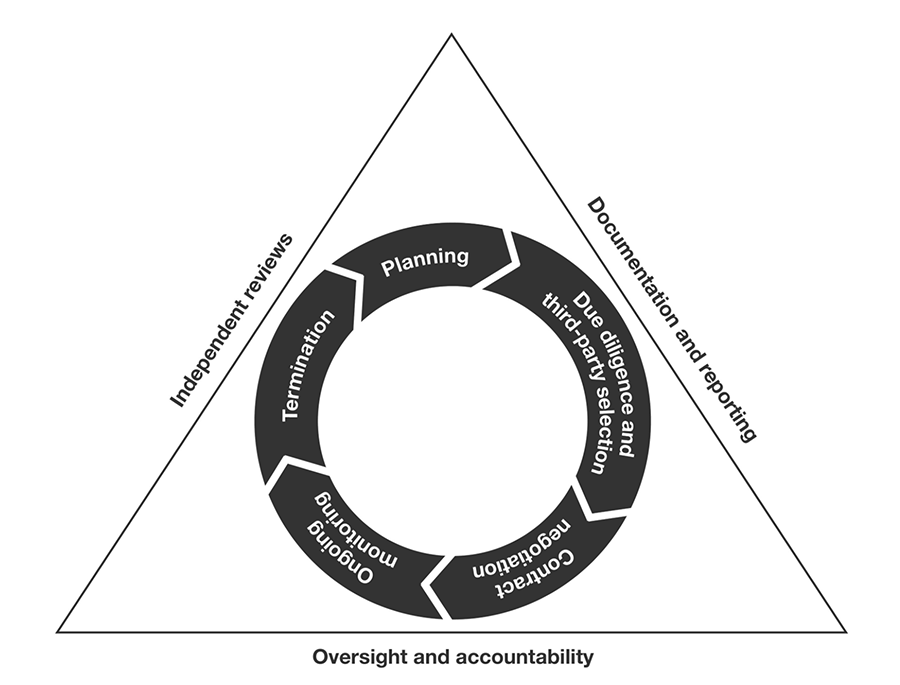
Source: Board, FDIC, and OCC
How to Comply with the Interagency Guidance on Third-Party Relationships
Each of the six principles in the Interagency Guidance on Third-Party Relationships maps to a stage of the third-party lifecycle. Here are key requirements and recommended best practices for each stage.
1. Planning
At the earliest stage of a third-party relationship, the Guidance recommends evaluating the types and nature of risks in the relationship and developing a plan to manage the relationship and its related risks. As part of the process to establish or refine your third-party risk management program, consider:
- Governing policies, standards, systems and processes to protect systems and data
- Roles and responsibilities (e.g., RACI) of all team members involved
- Third-party inventories to understand the scale and scope of third-party involvement
- Third-party classification and categorization approaches
- Risk scoring and thresholds based on your organization’s risk tolerance
- Assessment and monitoring methodologies based on third-party criticality
- Fourth- and Nth-party involvement in delivering critical services
- Sources of continuous monitoring data (cyber, business, reputational, financial)
- Key performance indicators (KPIs) and key risk indicators (KRIs) to measure your program and third parties
- Compliance and contractual reporting requirements
- Incident response processes
- Internal stakeholder reporting – for management and the Board
- Risk mitigation and remediation strategies
Each of these items is critical to building a comprehensive TPRM program plan.
Align Your TPRM Program with Interagency Guidance
The Interagency Guidance on Third-Party Relationships: Best Practices Guide examines the requirements that organizations should address at each stage of a third-party relationship.

2. Due Diligence and Third-Party Selection
Once a third party has been identified, it is essential to conduct thorough due diligence before selecting and entering into a contract. The Interagency Guidance on Third-Party Relationships suggests that due diligence should include assessing a third party’s ability to perform the activity as expected, adhering to policies, complying with all applicable laws, regulations, and requirements, and operating in a safe and sound manner.
Success that this stage requires assessing and monitoring third parties based on the extent of threats to information assets by capturing, tracking and quantifying inherent risks. Criteria used to calculate inherent risk includes:
- Type of content required to validate controls
- Criticality to business performance and operations
- Location(s) and related legal or regulatory considerations
- Level of reliance on fourth parties (to avoid concentration risk)
- Exposure to operational or client-facing processes
- Interaction with protected data
- Financial status and health
- Reputation
From this inherent risk assessment, your team can automatically tier third parties; set appropriate levels of further diligence; and determine the scope of ongoing assessments.
3. Contract Negotiation
The Guidance recommends reviewing existing contracts periodically, particularly those involving critical activities, to ensure they continue to address pertinent risk controls and legal protections.
Meeting this requirements means centralizing the distribution, discussion, retention and review of third party contracts so that all applicable teams can participate in contract reviews to ensure the appropriate clauses are included and managed.
Key practices to consider in managing third party contracts include:
- Centralized storage of contracts
- Tracking of all contracts and contract attributes such as type, key dates, value, reminders, and status – with customized, role-based views
- Workflow capabilities (based on user or contract type) to automate the contract management lifecycle
- Automated reminders and overdue notices to streamline contract reviews
- Centralized contract discussion and comment tracking
- Contract and document storage with role-based permissions and audit trails of all access
- Version control tracking that supports offline contract and document edits
- Role-based permissions that enable allocation of duties, access to contracts, and read/write/modify access
Ensuring sound contract lifecycle management will enable the organization to effectively:
- Manage agreements and performance
- Enforce information retention, right-to-audit clauses and remediation measures
- Obtain compliance reporting
- Require business resilience and continuity
- Bring visibility into subcontracting and foreign-based third parties
4. Ongoing Monitoring
Successful third-party risk management programs include periodic internal controls-based assessments against industry standard frameworks and ongoing monitoring to confirm the quality and sustainability of the third party’s controls.
To accomplish this, continuously track and analyze external threats to third parties by monitoring the Internet and dark web for cyber threats and vulnerabilities, as well as public and private sources of reputational, sanctions and financial information.
Monitoring sources should include:
- Criminal forums; thousands of onion pages; dark web special access forums; threat feeds; and paste sites for leaked credentials — as well as several security communities, code repositories, and vulnerability databases
- Public and private sources of reputational information, including M&A activity, business news, negative news, operational updates, and more
- Financial performance, including turnover, profit and loss, shareholder funds, etc.
- Reputational, regulatory and sanctions sources including politically exposed person profiles, global sanctions lists, and regulatory and legal information
Correlate all monitoring data to assessment results and centralize in a unified risk register for each third party, streamlining risk review, reporting and response initiatives.
5. Termination
Organizations can be exposed to post-contract risk, yet research shows that few organizations conduct risk management at the end of a relationship. The Interagency Guidance says that it is important for management to terminate third-party relationships in an efficient manner, whether the activities are transitioned to another third party, brought in-house, or discontinued.
To streamline the vendor offboarding process, automate contract assessments and offboarding procedures to reduce your organization’s risk of post-contract exposure:
- Schedule tasks to review contracts to ensure all obligations have been met. Issue customizable contract assessments to evaluate status.
- Leverage customizable surveys and workflows report on system access, data destruction, access management, compliance with all relevant laws, final payments, and more.
- Centrally store and manage documents and certifications, such as NDAs, SLAs, SOWs and contracts. Leverage built-in automated document analysis based on AWS natural language processing and machine learning analytics to confirm key criteria are addressed.
- Take actionable steps to reduce third-party risk with built-in remediation recommendations and guidance.
- Visualize and address compliance requirements by automatically mapping assessment results to any regulation or framework.
Streamlining Compliance with the Interagency Guidance on Third-Party Relationships
Effectively addressing the requirements in the Guidance is virtually impossible if you rely on spreadsheets to collect, analyze, remediate and report on cybersecurity controls. With the Prevalent Third-Party Risk Management Platform, your financial services institution can automate and accelerate its compliance initiatives. The platform enables you to:
- Build a comprehensive, agile and mature third-party risk management program based on proven financial industry best practices
- Automate the identification and assessment of critical third parties based on their criticality to the organization
- Assess and continuously monitor third parties for multiple types of risks
- Deliver automated remediation recommendations to third parties to reduce residual risk
- Measure against contractual key performance indicators (KPIs) and key risk indicators (KRIs)
- Simplify regulatory and security framework audit reporting to multiple internal and external stakeholders
- Deliver prescriptive business continuity and incident response programs to ensure third parties have the policies and procedures in place to address emerging risks
- Securely offboard third parties with a prescriptive process to ensure the organization is not exposed to ongoing residual risk
To learn more about complying with the Interagency Guidance on Third-Party Relationships, download our best practices guide or contact us to schedule a demo.
-

Foreign Corrupt Practices Act (FCPA): How to Assess Third-Party Anti-Bribery...
On February 10, 2025, the Trump Administration announced a pause in FCPA enforcement actions while a...
02/11/2025
-

How to Meet EBA Guidelines for Managing Third-Party ESG Risks
The new EBA Guidelines require financial institutions to assess, monitor, and manage ESG risks in their...
01/22/2025
-

SIG 2025: Key Updates and Considerations
Uncover key changes in the Standard Information Gathering (SIG) Questionnaire for 2025 and learn what these...
12/16/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




