3 Keys to Hitting the Third-Party Risk Maturity Bullseye
I’m sure you’ve heard all the metaphors used to describe maturing a third-party risk management program: "It’s a journey!" "It’s a marathon; not a sprint!" "It takes a village!" Regardless of how you describe your TPRM program, your organization's board and executive leadership need to know that you can reduce third-party risk to acceptable levels. In my experience, getting there requires the "Three Ts" of Talent, Tools and Techniques. Thanks to one of my favorite Chief Security Officers for sharing this concept with me (you know who you are!).

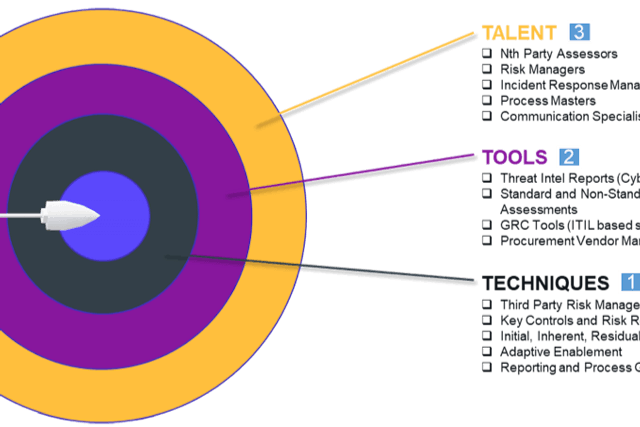
Hitting the third-party risk maturity bullseye requires the right mix of Talent, Technology and Techniques.
Talent
What makes a solid third-party risk team? I believe it's a team that ...
- understands the extended enterprise, knowing that the risk surface extends beyond direct, third-party vendors to the fourth- and nth-parties with which they do business;
- moves from assessing risk to managing risk because your assessments are just hollow scores if you can't manage identified risks down to acceptable levels;
- responds to incidents and trends based on a repeatable, sustainable and scalable model that leverages the right tools (see below);
- continuously improves its processes to remain agile in the face of changing risks; and,
- communicates well with vendors while negotiating effectively to ensure that key controls are properly applied to reduce risks.
Tools
While the word “tool” belittles the solutions, platforms and technologies designed to help manage third-party risk, it works with the theme of “Ts” 😉. Good solutions deliver ...
- threat intelligence reports to help assurance teams navigate the most important threats and quickly determine the right action to take;
- standard and non-standard questionnaire assessments to deliver wider organizational visibility into your vendors' internal controls, plus the ability to recommend remediations;
- standardized service tracking (ITIL or otherwise) so that your team has a predictable, programmatic language to use with vendors; and,
- procurement vendor management to help you get in front of the assessment lifecycle.
Techniques
The final "T" stands for Techniques, which are the processes, policies and procedures that enable your program to efficiently operate. Good techniques include ...
- a Third-Party Risk Management policy that expands on what may be in your Master Service Agreement (MSA) contract or Business Associate Agreement (BAA), detailing specific internal and external expectations for addressing risk;
- key controls and risk recommendations that align risk managers and vendors behind a single set of standards and expectations (this inevitably saves time and eliminates headaches);
- profiled, inherent, and residual risk processes that are clearly designed and defined;
- adaptive enablement to drive the internal and external process improvements that lead to a high level of security maturity; and,
- reporting and process governance that continuously evaluates your key performance and risk, while revealing the intelligence necessary to drive data-based decisions.
Which T should you focus on first?
That’s sort of a trick question. If you have an established third-party risk management program, then it really comes down to which area requires the most help to bring things into balance. Maybe you have some (possibly underused) tools, but you're lacking the people or processes to support them. Maybe you have great people but no tools or well-defined processes to support them. Or, you might have a great process without the right team or tools to execute it.
On the other hand, if you're in the early stages of your program, the best place to start is with "Techniques." Set the foundation for the program with solid processes and procedures, and you can then build a team of experts and support them with the right tools.
Are three Ts must be present to hit the target of third-party risk maturity. Going back to my metaphors at the beginning of this blog, it’s a journey that is unique to your organization. It might take a few years to get there, but the right mix of people, process and technology will speed you along.
If you're curious to what degree your Talent, Tools and Techniques are supporting your third-party risk efforts, I recommend you engage with one of our third-party risk management specialists for a complementary, one-hour maturity assessment. The session will produce a report outlining a specific roadmap for addressing any shortcomings in your third-party risk management program.
Contact us to schedule your personalized TPRM maturity assessment today!
-

Third-Party Risk Management: The Definitive Guide
Third-Party Risk Management (TPRM) has advanced from being an annual checklist exercise to a critical daily...
01/23/2025
-

Vendor Due Diligence Strategy and Checklist
With a mature vendor due diligence strategy, businesses can assess risks early, categorize vendors accordingly, and...
01/16/2025
-

The Top 7 TPRM Predictions for 2025
2025 promises to be a consequential year for third-party risk management. Read our top TPRM predictions...
12/12/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




