2023 Third-Party Risk Management Study: Warning! Turbulence Ahead

2022 was a turbulent year for the practice of third-party risk management (TPRM), as evidenced by the results of the annual Prevalent Third-Party Risk Management Study. Over the past year, organizations dealt with the fallout from the Russian invasion of Ukraine and resulting supply chain disruptions, damaging and widespread third-party breaches and security incidents (like LastPass, OpenSSL, Okta, Toyota, and several in healthcare), and emerging regulatory oversight in areas beyond IT security (like ESG).
While organizations have gained some “elevation” by maturing their TPRM programs since last year’s study, many still have more work to do to ensure a smooth journey moving forward. The 2023 study reveals that third-party risk management practitioners can chart a better course by:
- Automating response to third-party incidents. Too many organizations report using manual processes and a complex array of tools to understand and resolve vendor breaches.
- Building a single source of the truth. More teams are getting involved in third-party risk management, but the use of multiple overlapping tools presents a foggy picture of risk.
- Giving up spreadsheets once and for all. Nearly half of companies still use spreadsheets to assess their third parties – and many are not confident in the results!
- Remediating third-party risks. The point of a TPRM program is to reduce risk, but the study exposes a wide gap between rates of risk assessment and risk remediation.
In this post we’ll preview the results of the study and recommend four steps that your organization can take today to reach TPRM cruising altitude.
The 2023 Third-Party Risk Management Study
Discover how organizations are addressing today’s third-party turbulence, reaching cruising altitude with their risk management processes, and staying ahead of future risks.

41% of companies experienced an impactful third-party breach in the last 12 months but rely on overlapping tools and manual processes for incident response
An overwhelming majority of companies (71%) report this year that the top concern regarding their usage of third parties was a data breach or other security incident due to poor vendor security practices.
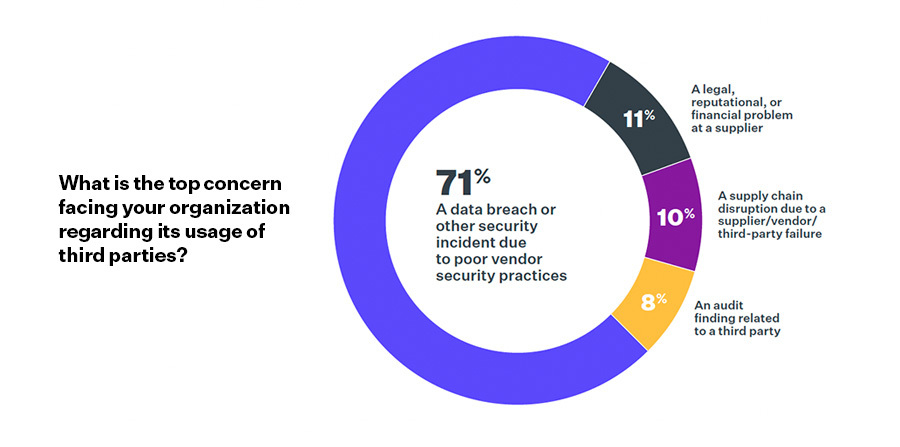
This should not come as a surprise as 41% of respondents reported experiencing a data breach and with a tangible impact in the last 12 months.
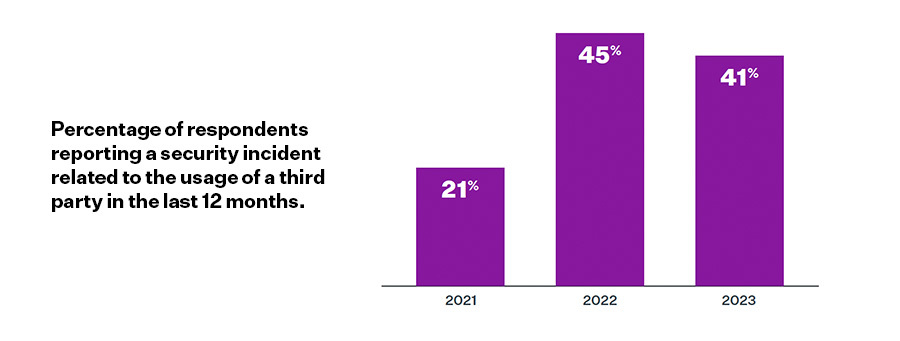
When incidents did occur, organizations reported having access to more response tools, such as Dark Web monitoring and data breach monitoring, versus in the previous year. See page 6 of the report for the full spectrum of tools and response processes used by respondents.
What you’ll see is that manual methods still persist, with a disappointingly large percentage of companies (54%) including manual spreadsheets as part of the mix and increasing usage of news feeds to learn about breaches. The silver lining? The number of companies not monitoring for third-party breaches dropped from 12% to 4%!
Third-party data breaches and security incidents are driving increased information security involvement in TPRM …
70% of respondents report that Information Security is more involved in third-party risk management, and 71% indicate that InfoSec now owns the TPRM program outright.
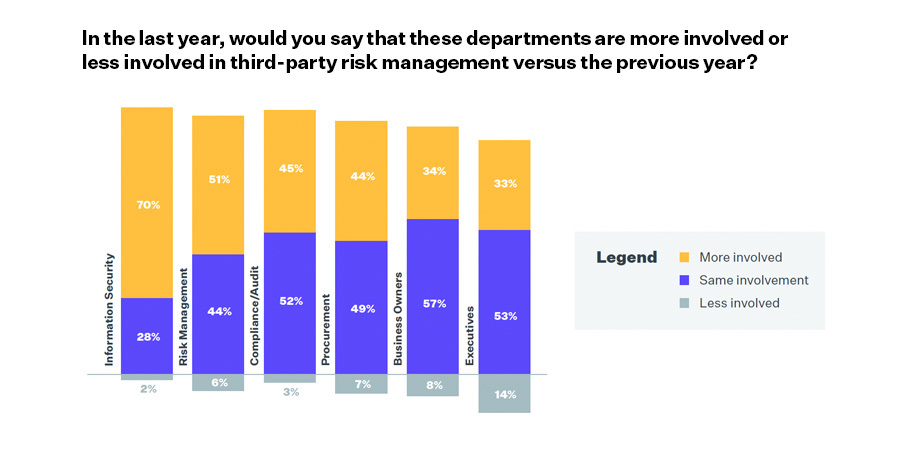

Read the full report to see how involved specific departments such as procurement, compliance/audit, risk management, and others are in the third-party risk management programs today (see page 11).
You’ll see that InfoSec was also the team most cited (at 57%) as the department responsible for setting the TPRM program strategy, and bearing the most responsibility (71%) for executing third-party assessments and monitoring.
We believe Infosec’s increased involvement and ownership signals greater adoption of third-party risk management as a standard security practice in organizations, perhaps advancing it toward the ranks of traditional security cornerstones like patch management and perimeter security.
… and engagement across the organization.
Continuing the data breach theme, 62% of respondents to this year’s study indicated that third-party data breaches and security incidents were top drivers behind increased involvement in third-party risk management.
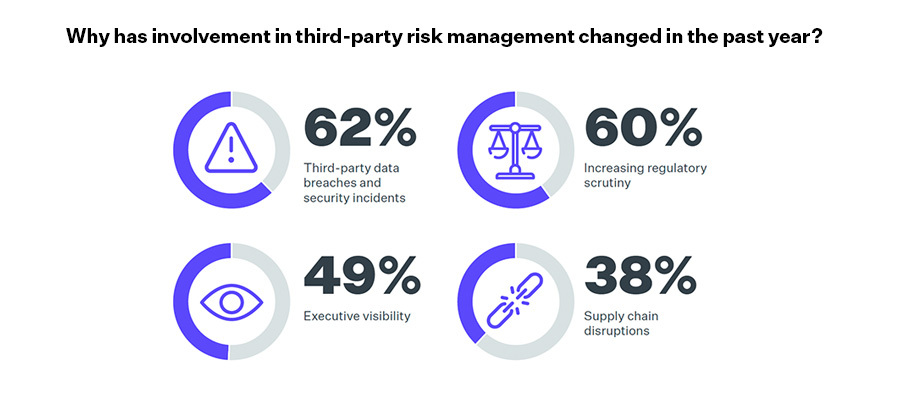
While InfoSec became the majority stakeholders in third-party risk management over the past year, all departments increased their involvement in TPRM since 2022. So, TPRM is still a team sport that relies on contributions from several departments with distinct priorities.
Discover which TPRM goals are most important to each department on page 12 of the report.
Nearly half of companies refuse to give up their spreadsheets, and many are unsure if their current risk assessment methods are even working!
A disappointing trend continues in 2023 as a growing number of organizations (48%) are using spreadsheets to assess their third parties. This percentage is up from 2022 and 2021, where 45% and 42% of companies, respectively, said they were using spreadsheets.

Check page 14 of the report to see how respondents are feeling about their approaches third-party risk assessment.
It won’t surprise you that a large percentage of companies responded “Unsure” when asked if their current method of assessing risks throughout the lifecycle, assessing multiple risk types, reporting and incident response was working. Manual methods just aren’t cutting it.
There is an upside in the data, however. Only 4% of respondents indicated that they are not currently assessing third parties at all, which continues a downward trend from 2021 (10%) and 2022 (8%).
In looking at the usage of different assessment methods on page 14 of the report, there are several with usage reported by more than 25% of respondents. However, the fact that organizations use multiple assessment tools begs the questions:
- Are these manual methods and disjointed toolsets meeting objectives to reduce third-party risk? and
- With all these tools in place, are organizations able to efficiently and cost-effectively manage third-party risk?
There is a HUGE gap between tracking and remediating risks across the lifecycle – and an average of 20% of companies are doing nothing at all!
Not surprisingly, the Offboarding and Termination stage of the third-party relationship lifecycle sees the lowest percentage of companies tracking (47%) and remediating (38%) risks, and the highest percentage of companies doing nothing at all (39%).

However, it’s the disparity between tracking risks and actually doing something about those risks, or remediating them, that is the big shocker here. The significant gap between tracking and remediating risks in the Initial Assessment and Sourcing & Pre-Contract Due Diligence stages is especially surprising, as these are the primary stages to discover and remediate risks before they impact the organization! In fact, about 20% of companies on average don’t appear to be tracking or remediating risks at all!
See how big this gap is for each stage of the third-party lifecycle by skipping to page 16 of the full report.
Organizations struggle with manual processes to manage risks across the lifecycle.
Of the seven stages of the third-party risk lifecycle, five are still presenting clear challenges stemming from a preponderance of manual processes. This should not come as a surprise, as spreadsheets still represent the #1 method of assessing third-party risk (48%, see Finding #2) and are used mostly at the Sourcing/Pre-Contract Due Diligence stage (31%). Perhaps this is the reason behind the gap between tracking and remediating risks (see Finding #4) – it just can’t be done efficiently.
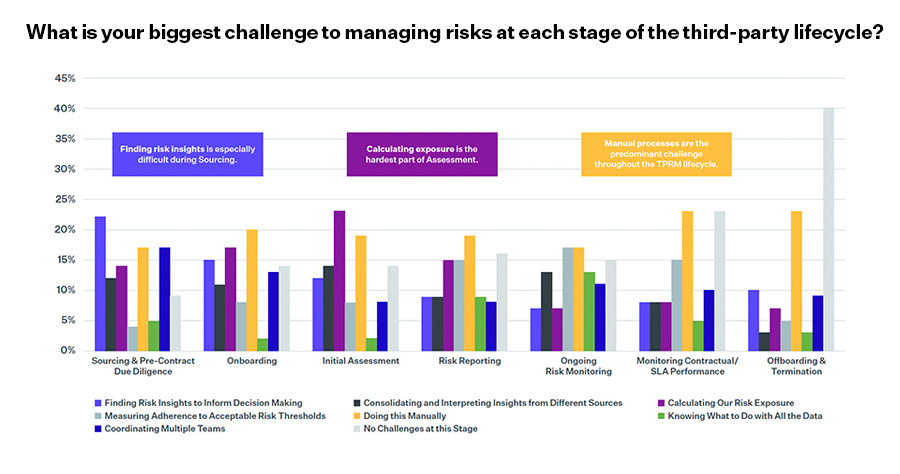
The usage of manual tools might be behind the challenges that companies face in managing risks across the lifecycle.

Notable in this year’s response data is the usage of multiple different tools to track and manage risk at the different stages of the lifecycle. We asked survey respondents about their primary tools for each stage, and we report our findings on page 18 of the full report.
The critical question here is: With so many different tools at their disposal, why are organizations still struggling with manual processes?
The 2023 TPRM Study Infographic
Review key statistics from our study of organizations trying to chart a course to TPRM success.

4 Best Practices Recommendations to Ensure a Smooth TPRM Flight
The results of this study demonstrate that third-party risk management is gaining elevation in enterprises, but many programs haven’t reached maximum airspeed yet due to the effects of manual processes and siloed tools.
NOTE: For the full recommendation details, download the study results paper.
1. Automate Incident Response to Reduce Costs and Risk Exposure
Time is money, so shortening the gap between incident discovery and mitigation can reduce costs and limit the company’s risk exposure – but that means you have to automate incident response processes. No more spreadsheets or overlapping tools that only tell part of the incident’s origin story!
2. Build a Single Source of the Truth to Knock Down Siloes and Extend Risk Visibility Throughout the Enterprise
Results from this study show that, although information security risks are considered the most important, multiple enterprise teams are involved in third-party risk management – each with their own goals, workflows, assessment processes, and risks to review.
Yet, we see a high percentage of companies that are using multiple tools (including spreadsheets) to assess vendors and are unsure of whether their current methods are hitting the mark, or even delivering consolidated insights across risk areas.
A better approach is to unify all internal teams with a single set of workflows, third-party risk profiles, assessments, and reporting.
3. Give Up Spreadsheets Once and for All and Automate Assessment and Monitoring Processes Across the Lifecycle
Almost of half of organizations are still using spreadsheets to assess third parties. This study also shows that organizations are challenged by manual processes (like spreadsheets) in 5 of the 7 stages of the third-party risk lifecycle. Therefore, look for a solution that centralizes contract lifecycle management; offers remediation guidance to ensure offboarded vendors meet your company’s compliance and security requirements to an acceptable level of risk; and delivers a prescriptive process to address final tasks and report according to compliance requirements. You can’t accomplish any of this with a spreadsheet!
4. For Goodness Sake, Remediate!
Data from this study shows a significant fall-off between risk tracking and remediation. You can’t call it risk management if you’re not actually going to manage the risks! To remediate risks down to an acceptable level to the business (or to require proof of compensating controls in the place of specific remediations), leverage a third-party risk management platform.
Take the Next Steps Toward TPRM Cruising Altitude
Download the full e-book and infographic for additional statistics, context and recommendations to benchmark your existing TPRM practices. Then, request a demo for a strategy session with a TPRM expert.
-

Mitratech Named a Leader Once Again in the 2024 QKS...
Read an analysis of vendor risk management market trends and key solution evaluation criteria.
11/18/2024
-

61% of Companies Have Been Breached by a Third Party...
Read the findings from our annual TPRM study and implement these best practices to put out...
05/08/2024
-

2023 Gartner® Market Guide for Supplier Risk Management Solutions Cites...
Prevalent believes it is differentiated by delivering comprehensive coverage of multiple risk types and by delivering...
12/12/2023
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




